Multi-Factor Authentication (MFA) helps protect users by making it more difficult for someone else to sign in to their NHSmail account. It uses two different forms of identity: the user’s password, and a contact method.
This article is intended to provide Local Administrators with an overview of the process to enable MFA for NHSmail users. For more information on MFA, please refer to additional guidance for Local Administrators.
MFA Adoption Toolkit
We have created a toolkit to support local admins and local organisations with their MFA rollout. Please visit this page for more information.
MFA Enablement
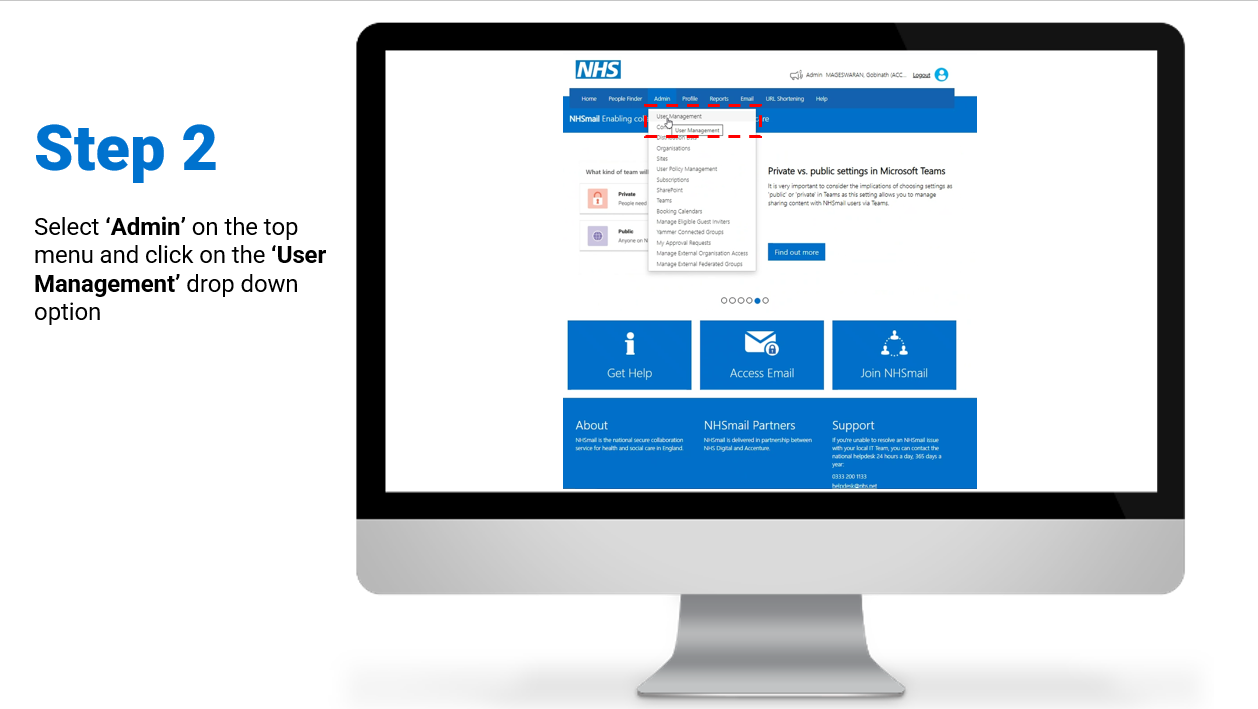
As a Local Administrator, you will be able to enable MFA for users via the Portal, either individually or in bulk. You can select users to enable MFA for by using filters available through the column picker, for example by organisation, organisation unit or user policy. Please note that there is currently a limit of 50 users at a time for the bulk edit feature. This can be repeated unlimited times for larger cohorts of users.
For information on how Local Administrators can temporarily disable MFA for users, please view the MFA Short and Long Term Exceptions Admin Guide
To see the MFA statuses of users at your organisation, you can download the MFA Status report from the Admin Reports section in Portal. For an overview of the reports alongside the other available admin reports, please refer here.
Below gives descriptions of each MFA Status that you will see on the MFA Status report
User Enabled – when a user enables MFA via the Self-Enrol Flow
User Disabled – when a user disables MFA via the Self-Enrol Flow
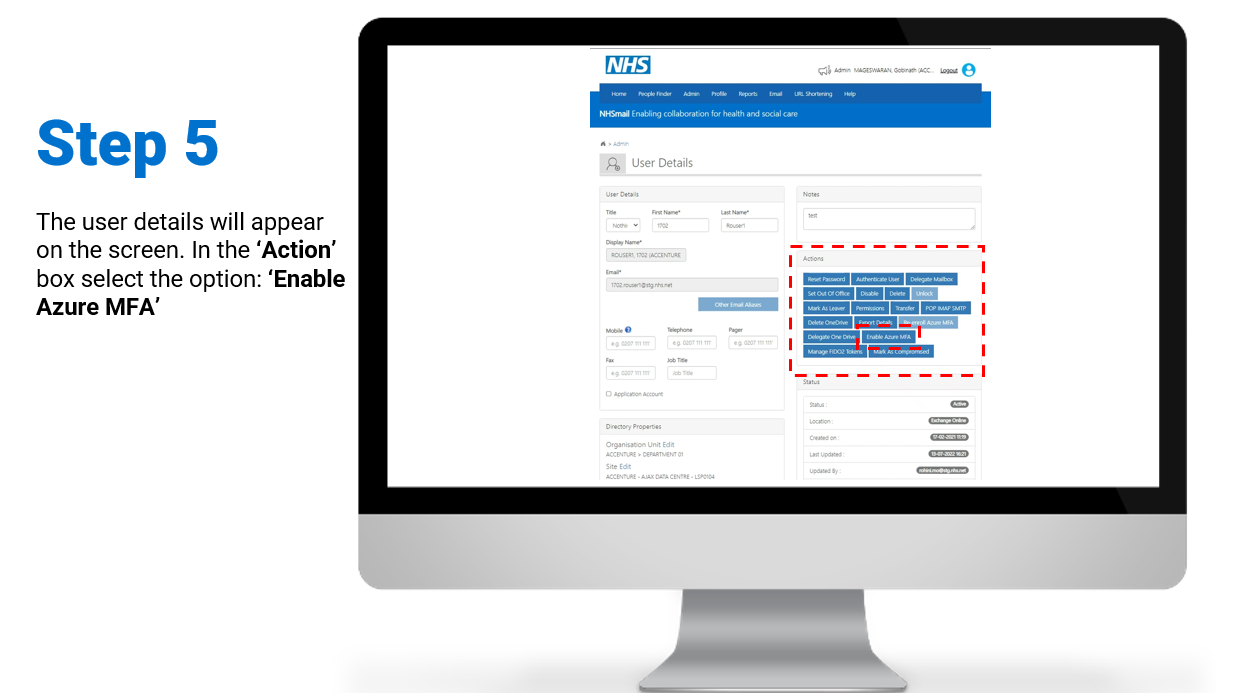
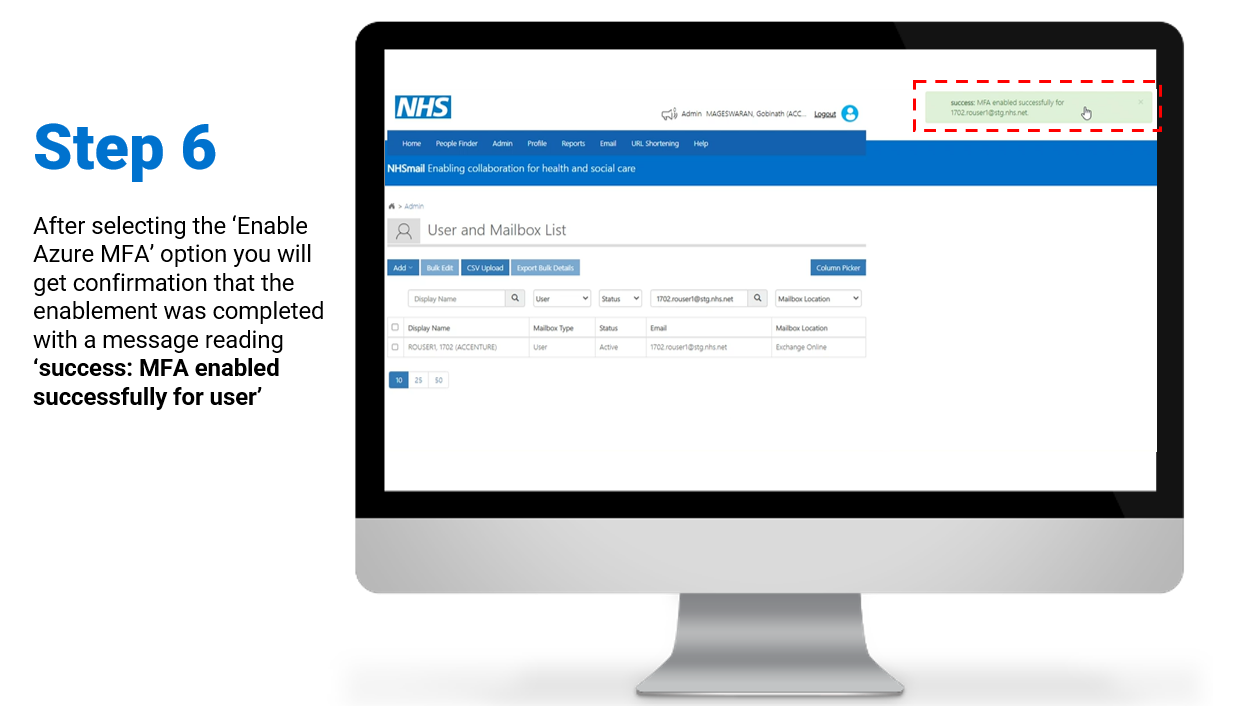
Admin Enabled – when a Local Admin enables MFA via User Management
Admin Disabled – when a Local Admin disables MFA via User Management
MFA Enforced ATP Group – for a user that is added to an ATP Role (this act enables MFA for this user) – This applies for when granted ATP Approver through the DL and also when added to a ATP group.
MFA Disabled ATP Group – for a user that was previously removed from an ATP Role (this acts as disabling MFA for this user) before Hawkins release (February 2024).
MFA Enforced Admin Role – for a user that is given an admin role (Local Admin, Primary Local Admin, Global Admin, Global Helpdesk etc)
MFA Disabled Admin Role – If (Local Admin, Primary Local Admin, Global Admin, Global Helpdesk etc) roles were removed from the user account before Hawkins release (February 2024).
MFA Enforced Compromised – for a user whose account has been marked as compromised
MFA 24 Hour Exception – for a user who has been granted a short-term exception
MFA Long Term Exception – for a user who has been granted a 180-day exception
The report also details Authentication Type used when signing in. The different types and their descriptions are outlined as follows:
Legacy Authentication Types:
OneWaySMS – A text message sent to the user
PhoneAppNotification – A notification is triggered to the user’s dedicated mobile application for authentication which will prompt for approval or rejection
PhoneAppOTP – A one-time unique passcode that will be displayed on the user’s dedicated application
TwoWayVoiceMobile – A mobile phone call where authentication will be granted upon the user entering a key
TwoWayVoiceAlternateMobile – A mobile phone call where authentication will be granted upon the user entering a key, for the user’s alternate registered mobile device
TwoWayVoiceOffice – A mobile phone call where authentication will be granted upon the user entering a key, for the user’s registered office phone
New Authentication Types:
SMS – A text message sent to the user.
Voice – A automated voice call made to the phone number registered by the user. The authentication will be granted once the user is prompted to press ‘#’ on their keypad.
PhoneAppNotification – A notification is triggered to the user’s dedicated mobile application for authentication which will prompt for approval or rejection.
PhoneAppOTP – A One-Time Passcode (OTP) sent to the user’s dedicated mobile application for authentication when prompted for an OTP value.
SoftwareOTP – A auto-generated One-Time Software Passcode (OTP) pushed to an authentication mobile app for the user to input the code value for authentication. Please view this article for more information on how to configure Software Time-Based One-Time (TOTP) tokens.
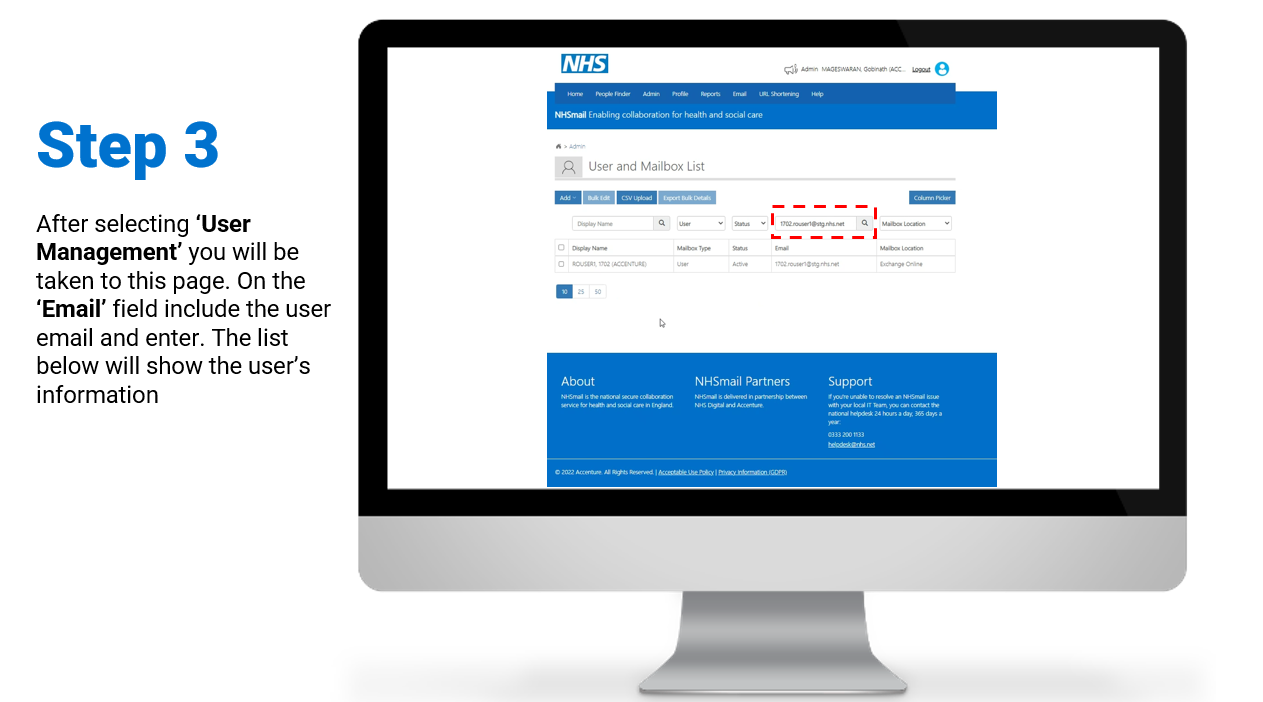
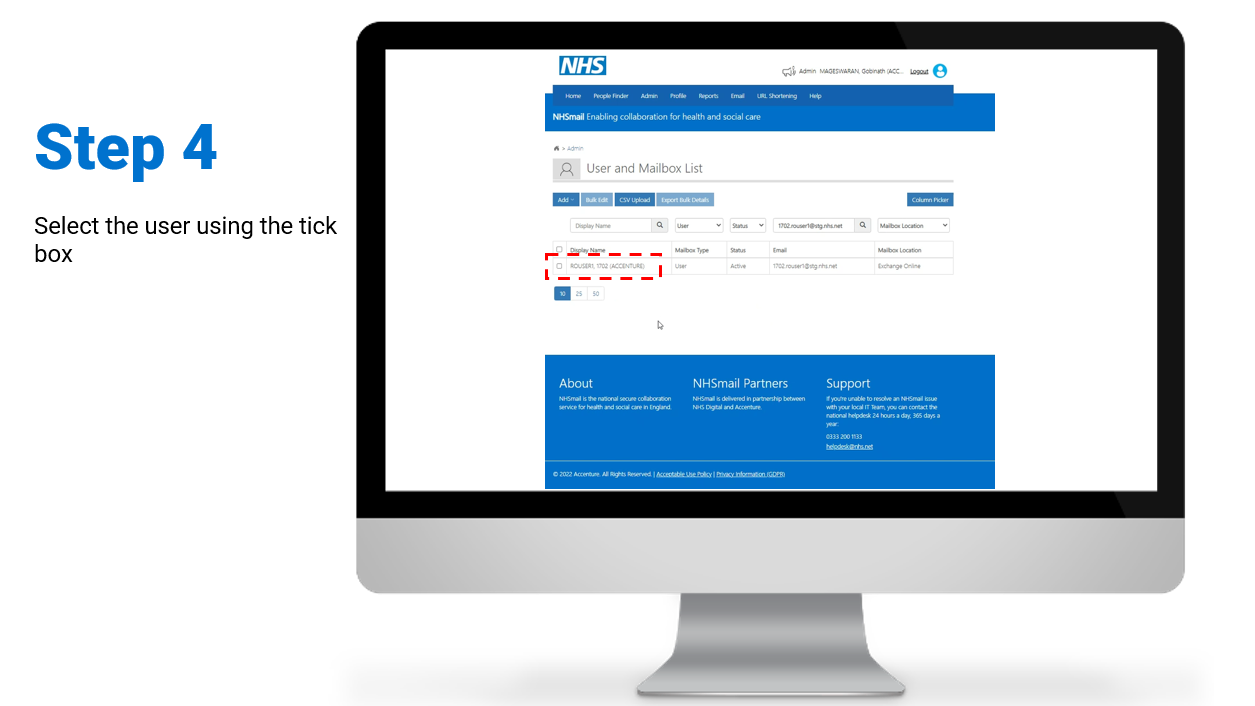
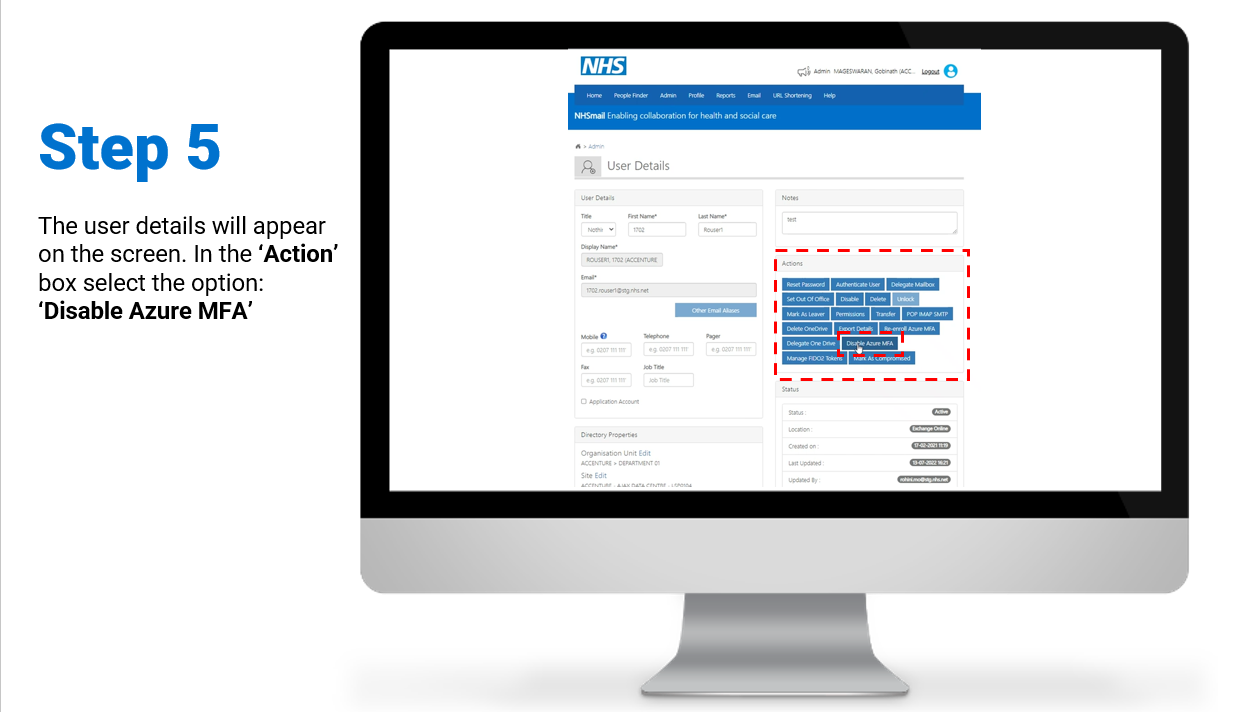
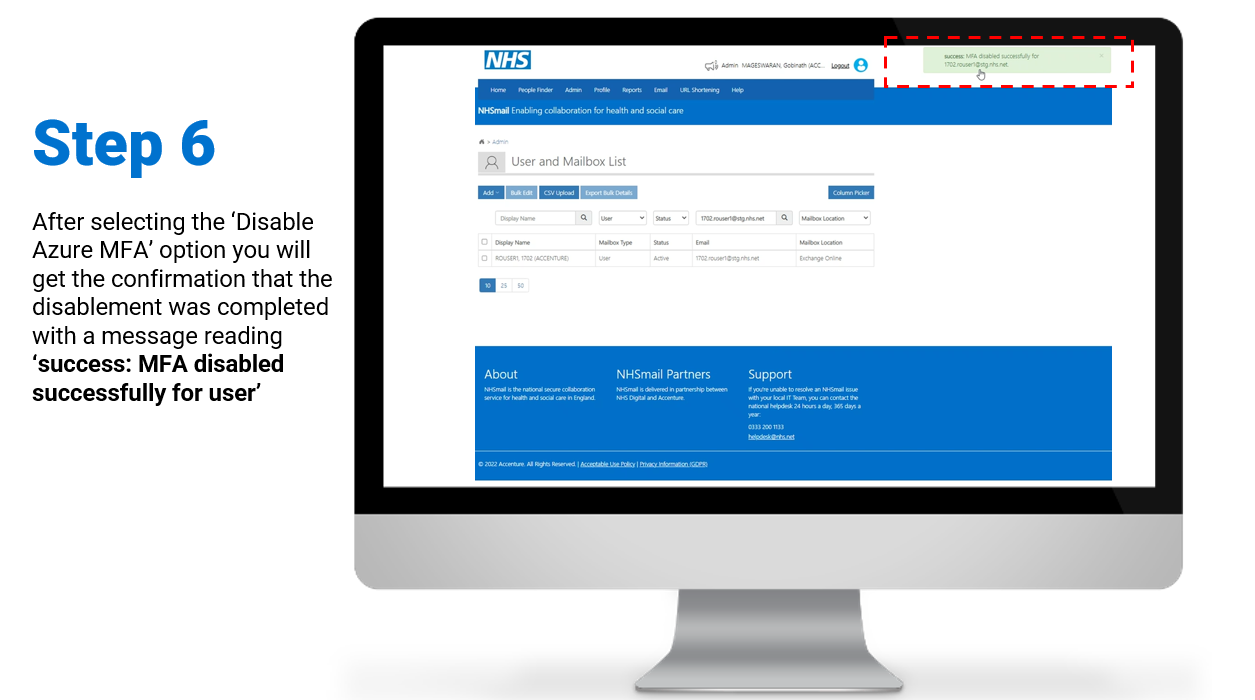
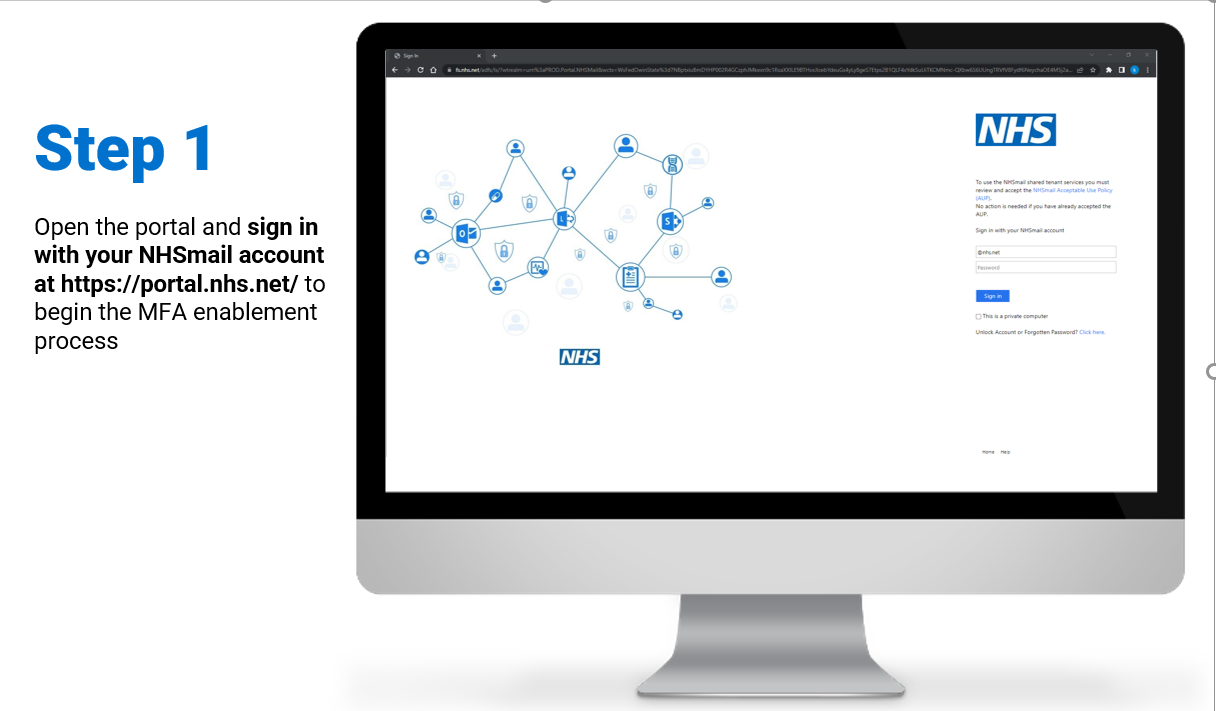
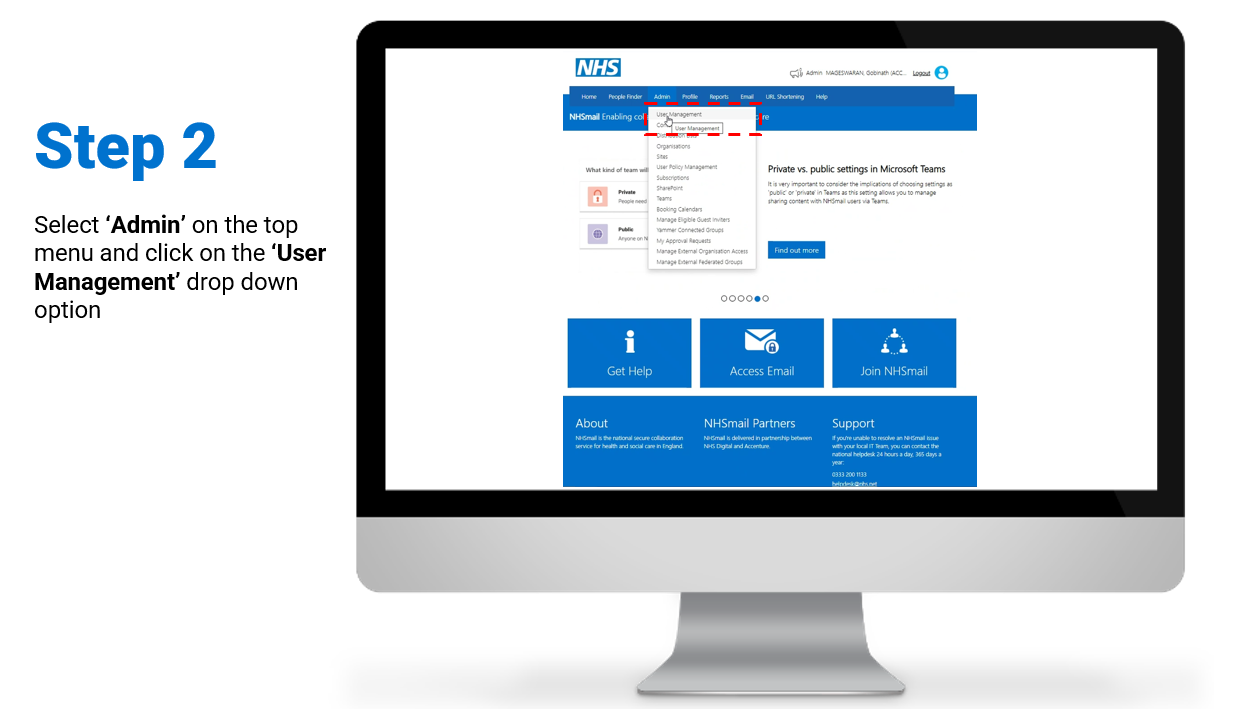
Individual – Enablement / Disablement of MFA
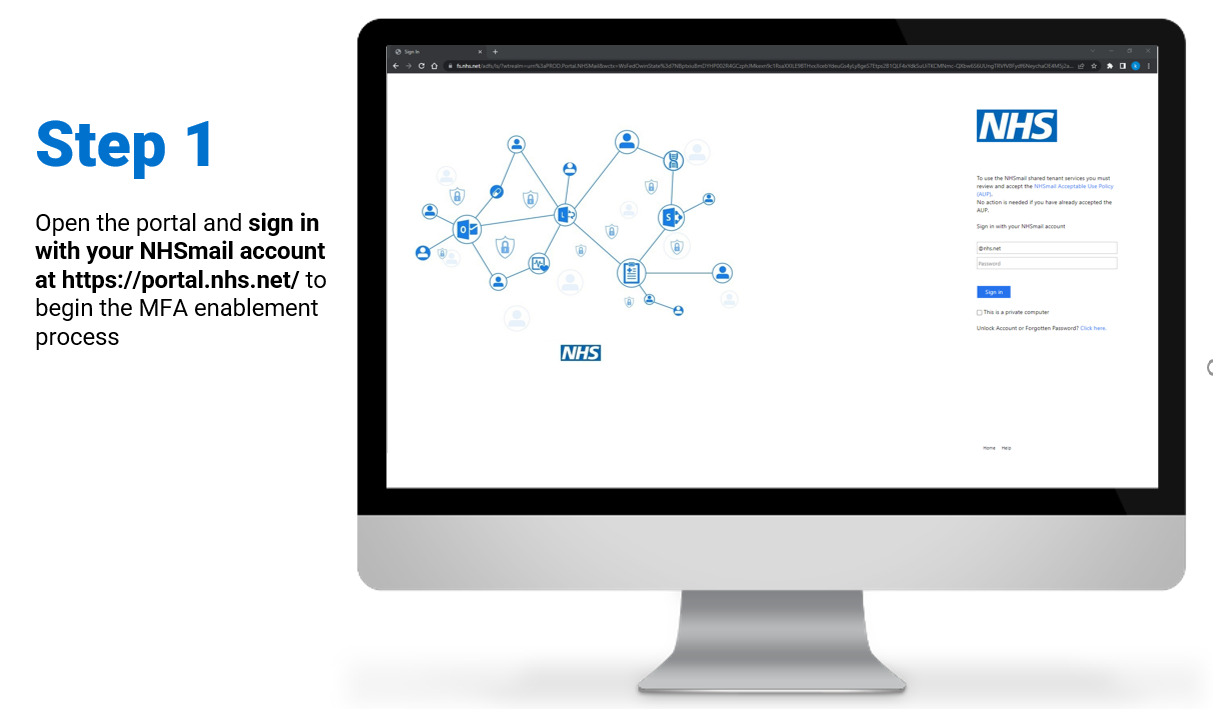
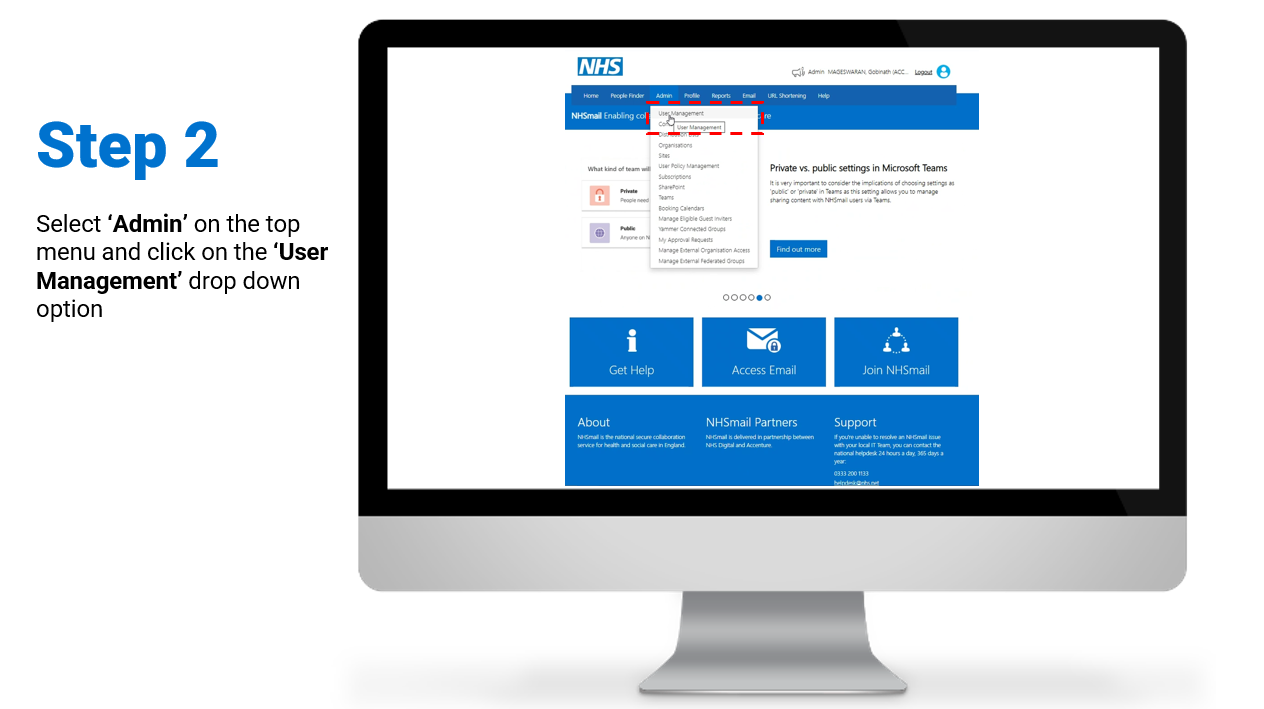
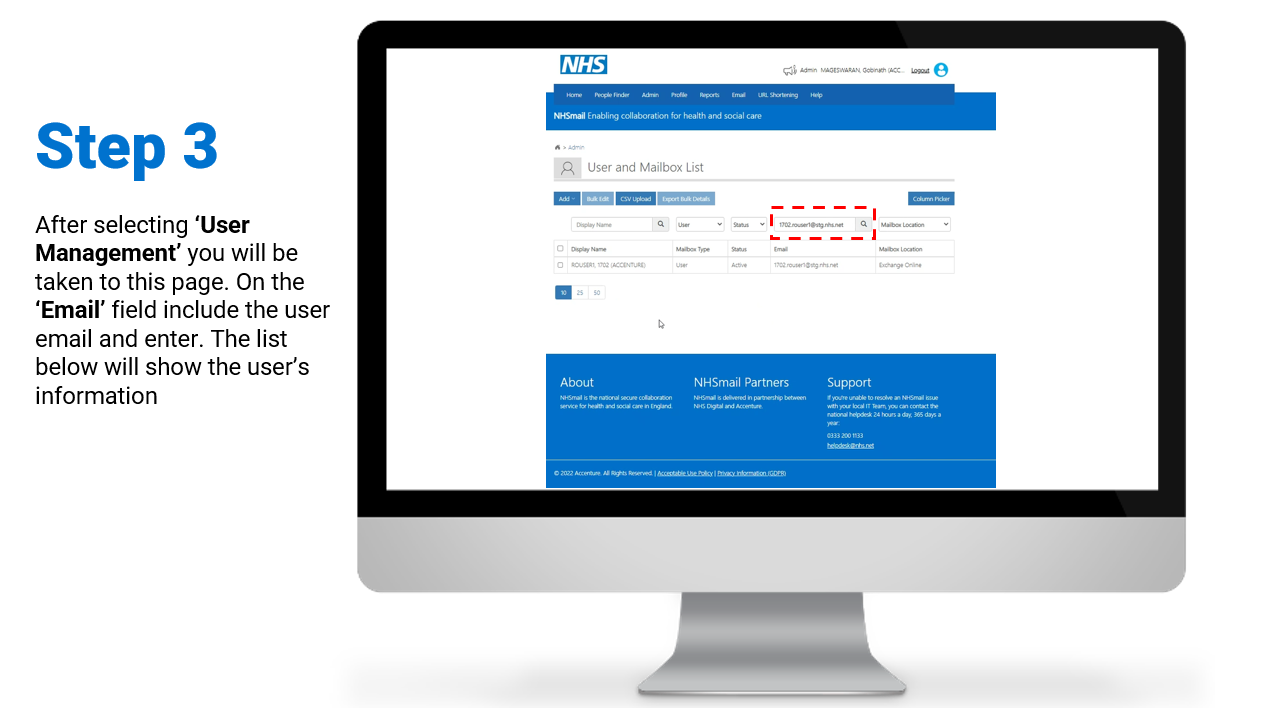
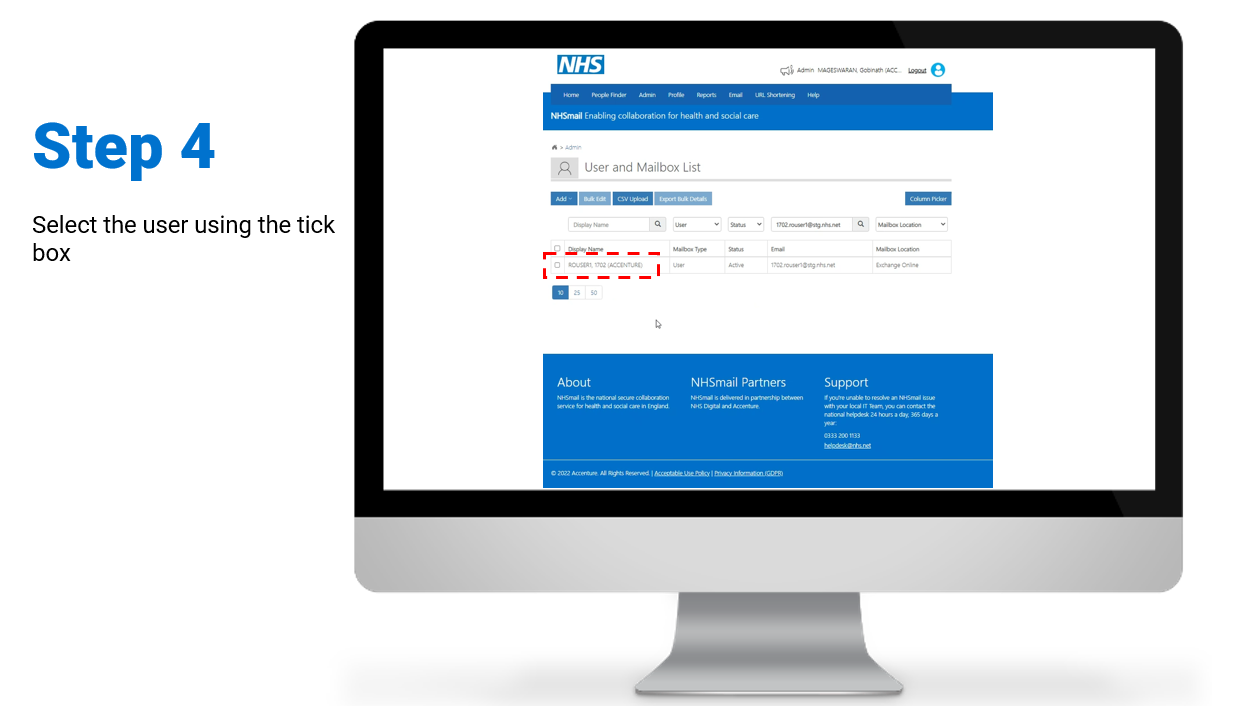
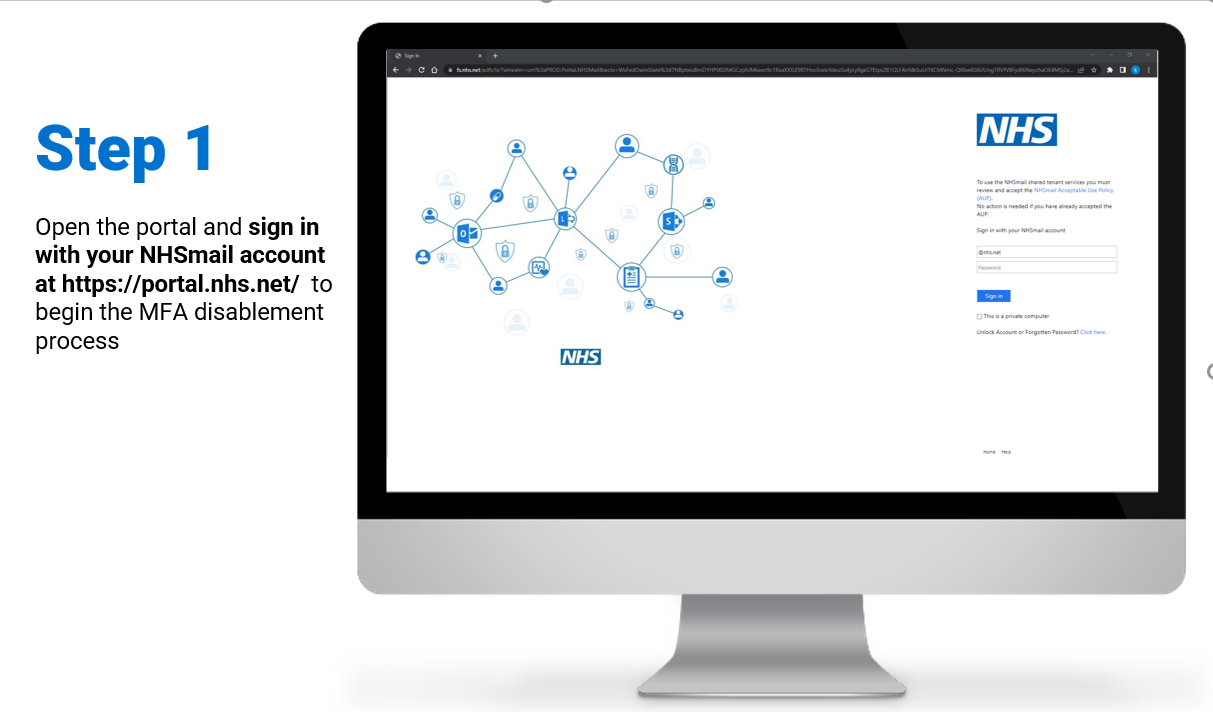
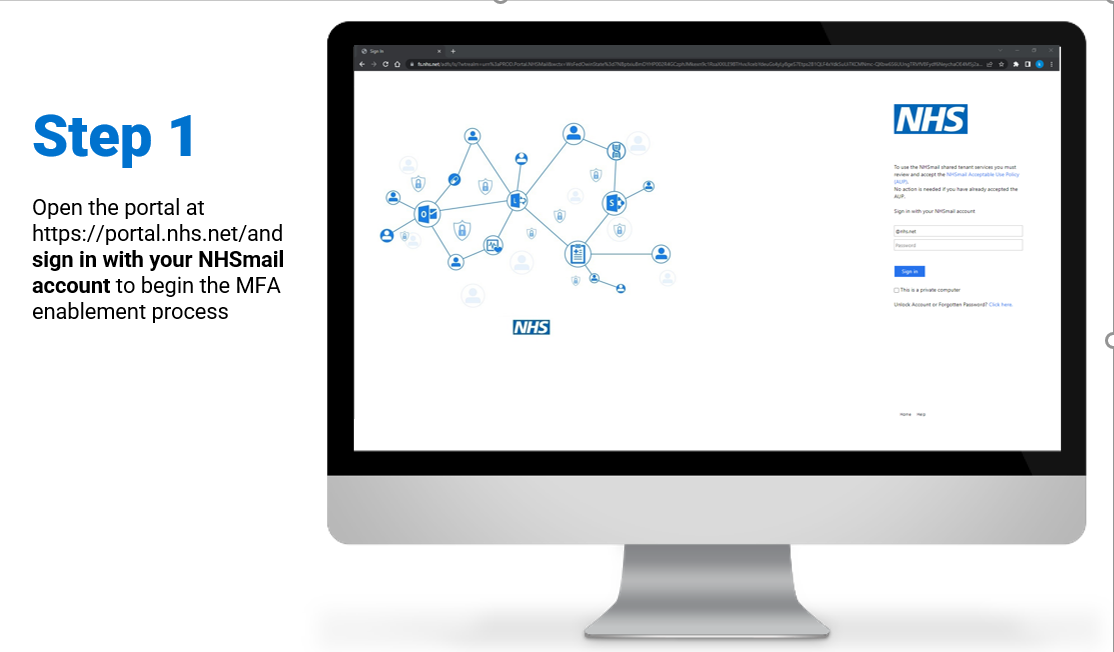
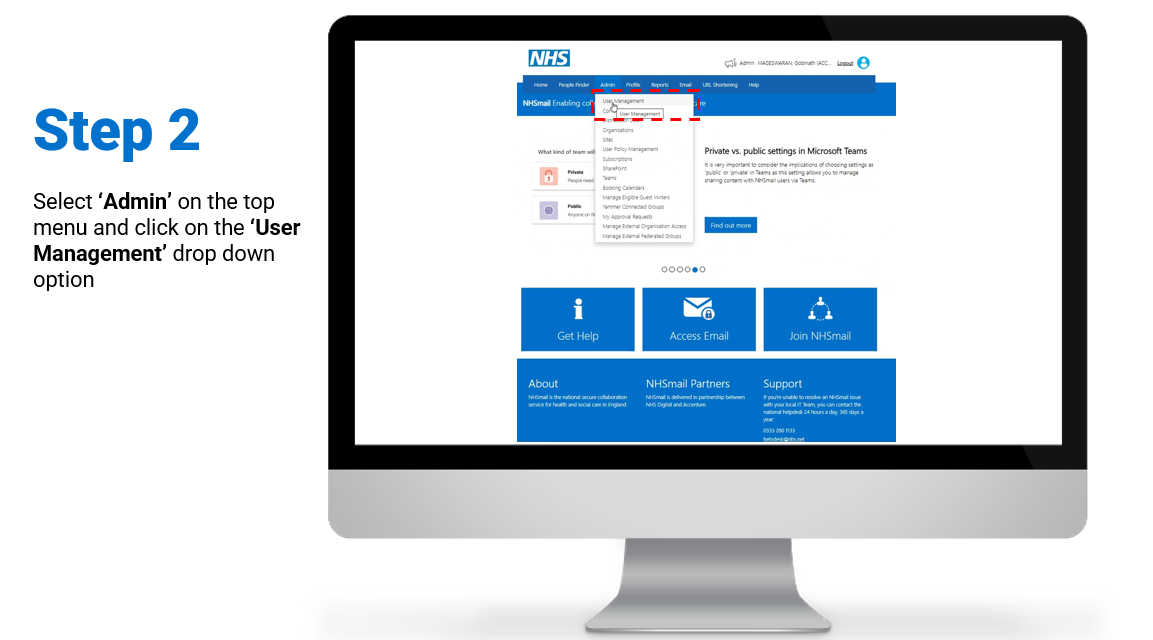
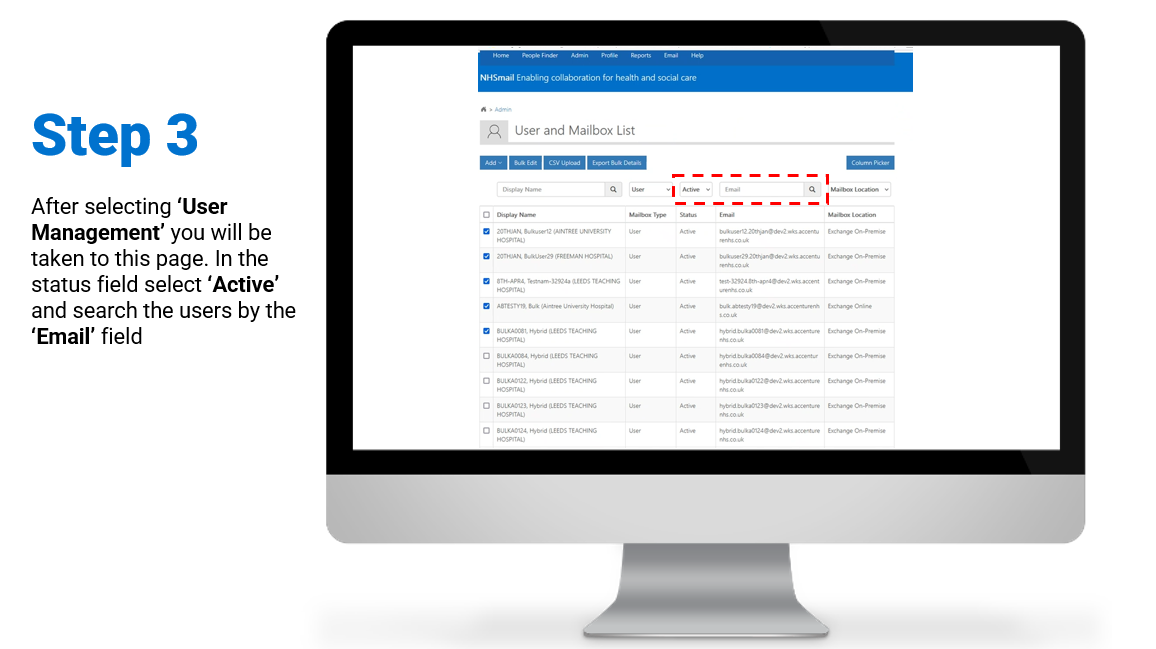
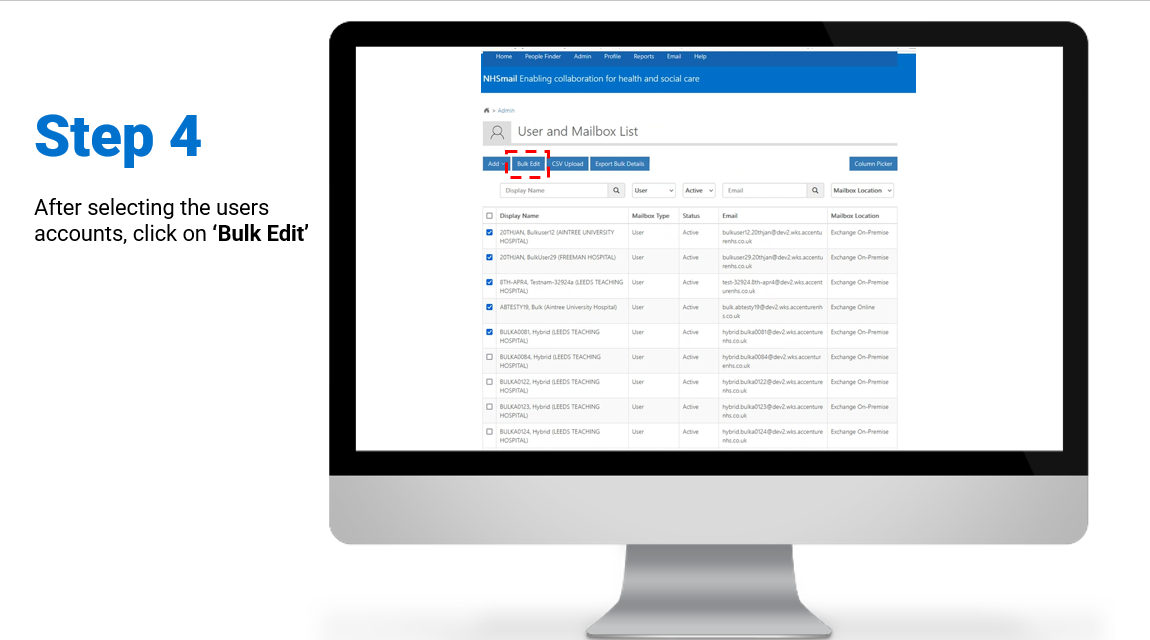
Steps on how to enable and/or disable MFA for individual user accounts:
To review/download the steps for individual enablement, click here.
To review/download the steps for individual disablement, click here.
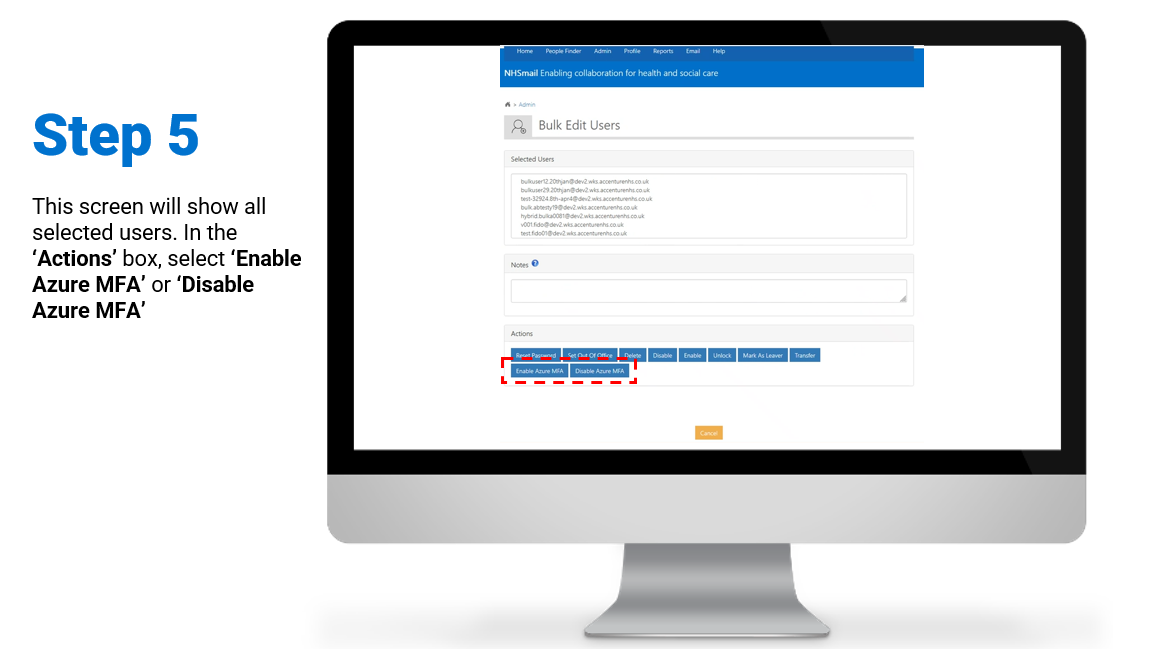
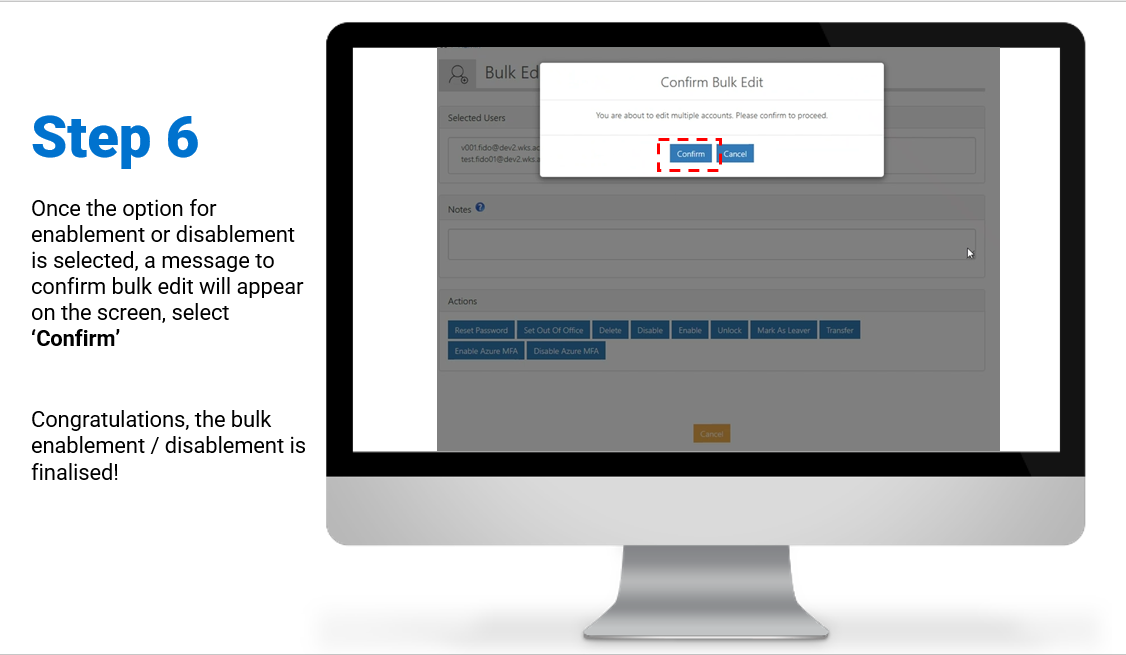
Bulk – Enablement / Disablement of MFA
Steps on how to enable and/or disable MFA for a group of user accounts:
To review/download the steps for bulk enablement and disablement, click here.
For requests over 50 mailboxes, please see the interim process here.
Please note it is also possible to bulk enable MFA on inactive accounts .
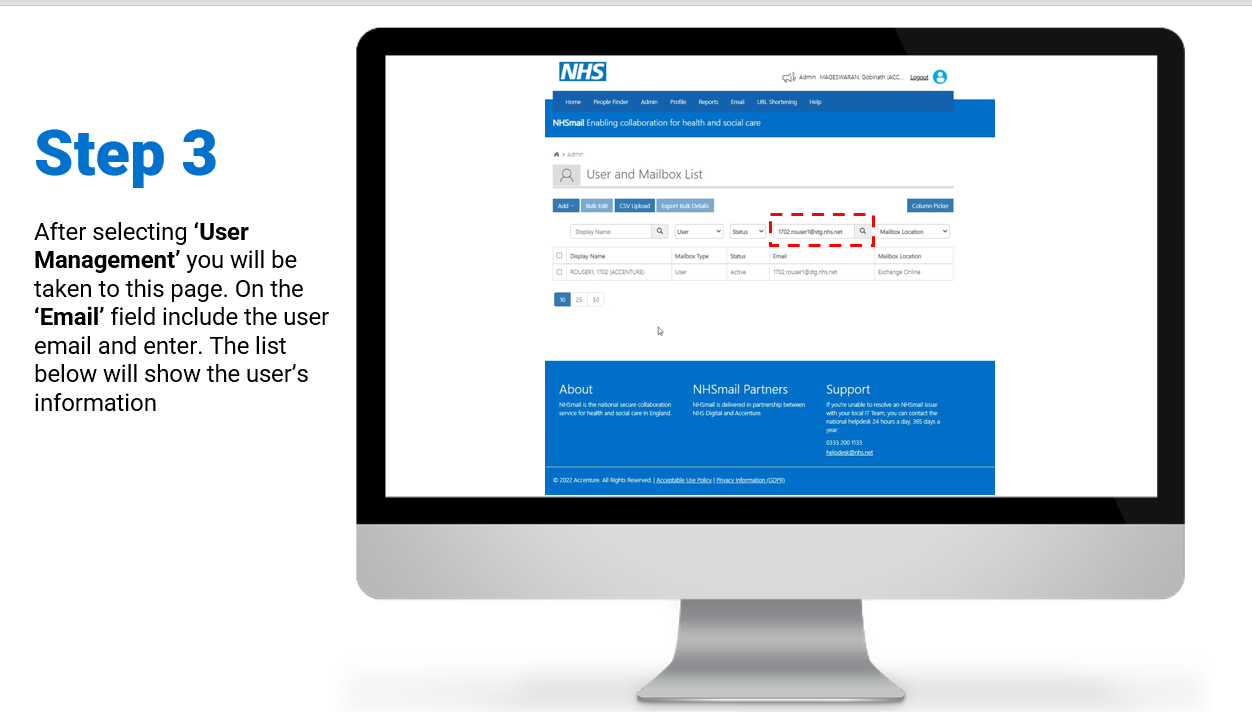
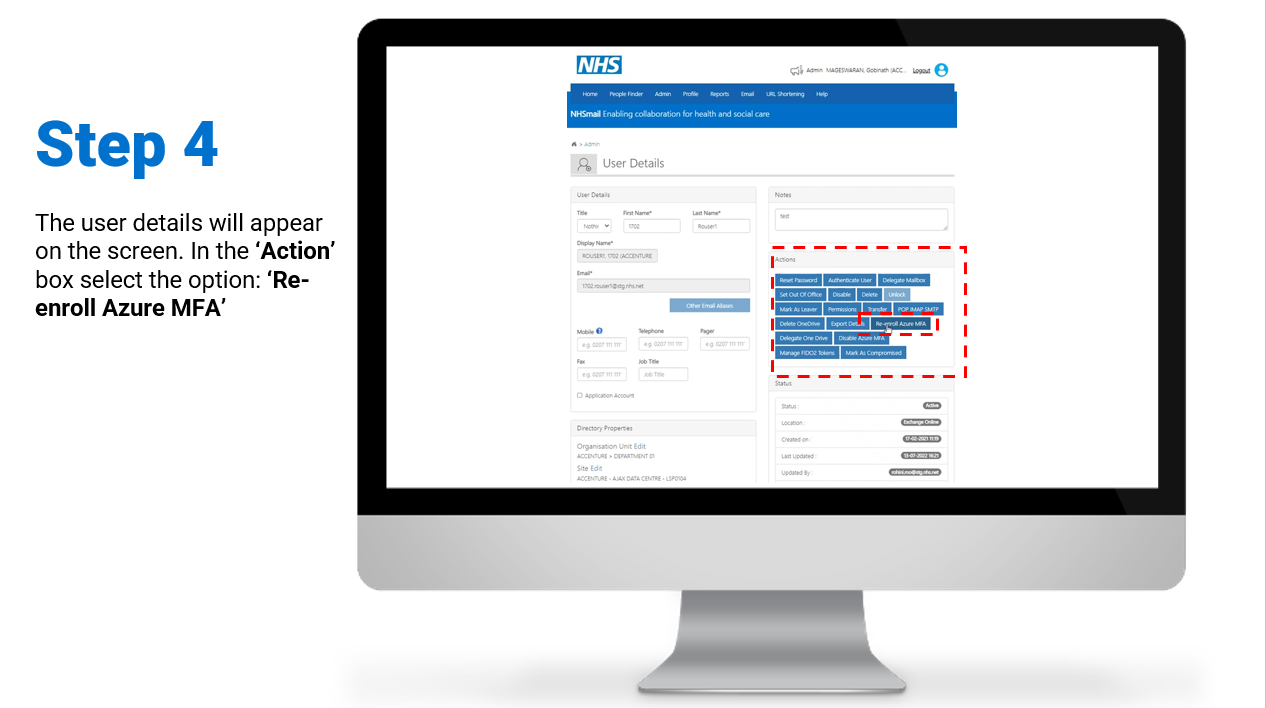
MFA Re-Enrolment
Steps on how to re-enrol user accounts for MFA:
To review/download the steps for MFA re-enrolment, click here. Please refer to Re-enrolling Per User and Conditional Access Multi-Factor Authentication for more information.
| Last Reviewed Date | 04/04/2024 |