This article provides high level instructions to support in effective device management via the NHSmail Intune Portal. Please visit the Operations Guide for more detailed guidance and support if required.
1. Managing Devices via Intune Portal
LAs can complete most enrolment and management tasks associated with device management (except for Group Management) via the Intune Portal (also referred to as Endpoint Manager).
The management of devices via the Intune Portal is available via the Role Based Access Controls (RBAC) and Scope Tags. These effectively give LAs the ability to configure items separately from other organisations. For more information on RBAC roles and Scope Tags, please refer to the Operations Guide.
2. Assigning Groups to Devices
Local Administrators belonging to onboarded organisations can create and manage Groups without requiring write access to Azure AD. The NHSmail Intune Security Group Management App allows granular control over the creating, editing and deletion of their organisation’s groups. It also permits LAs to closely and independently manage Groups scoped to their organisation including owners and Group members.
LAs can complete the following actions via the Security Group Management App (Step-by-step guidance can be found in the Operations Guide):
![]() View and Search Groups: LAs will be able to view and search all Groups assigned to the scope tagged ODS code in Intune.
View and Search Groups: LAs will be able to view and search all Groups assigned to the scope tagged ODS code in Intune.
![]() Create Gr5fv roups: LAs will be able to create Groups for users and Win 10 devices (excluding dynamic groups).
Create Gr5fv roups: LAs will be able to create Groups for users and Win 10 devices (excluding dynamic groups).
![]() Edit and Delete Existing Groups: LAs will be able to edit and delete existing Groups and will be able to view Group owners and members.
Edit and Delete Existing Groups: LAs will be able to edit and delete existing Groups and will be able to view Group owners and members.
![]() Add and Remove Group Members: LAs will be able to add and remove Group members for user groups and Win 10 device groups including with a csv. File and add and remove members to the organisation’s Intune Administration Group.
Add and Remove Group Members: LAs will be able to add and remove Group members for user groups and Win 10 device groups including with a csv. File and add and remove members to the organisation’s Intune Administration Group.
3. Assigning Policies
This section of the article covers the best practice recommendations for using Intune when assigning policies, settings and using assignment filters.
3.1 Dynamic vs. Assigned AAD Groups
AAD has two primary group types “Dynamic” and “Assigned” (also known as “Static”) groups.
- Assigned groups – Manually add users or devices into a static group.
- Dynamic groups – Automatically add users or devices to user groups or device groups based on an expression you create
These groups are used for policy assignments. LAs should become familiar as to which type of group to configure based on the specific scenario presented.
3.2 Device and User Groups
If you want to apply settings on a device, regardless of who is signed in, then the profiles must be assigned to the ‘devices group’. Settings applied to device groups always go with the device, not the user.
Profile settings applied to user groups always remain with the user and are applied at user level when signed in to their many devices.
3.3 Exclusion Groups
Exclusions takes precedence over inclusion for policies and apps in the below same-group type scenarios:
- Including user groups and excluding user groups.
- Including device groups and excluding device group.
For example, you can assign a device profile to an <ODS>-Intune-Users-Dentistry user group but exclude members in the <ODS>-Intune-Users-Dentistry-Senior Management Staff user group. Since both groups are user groups, all Dentistry users except the Senior Management staff get the profile.
3.4 Assignment Filters
Filters allow an admin to narrow the assignment scope of a policy within Intune. As an example, using filters allows you to target devices with a specific OS version or a specific manufacture. Filters provide the ideal solutions for scenarios such as:
- Deploying a device restriction policy to only iOS devices that are only a part of the dentistry department.
- Deploying an Android app to only android tablets in the audiology department users’ group.
Filters also provide the following benefits:
- Filters improve flexibility as well as granularity when it comes to assigning Intune policies and apps.
- They are used when assigning app, profiles, and policies. In addition they dynamically target devices that are based on the device properties entered.
- Can be used and reused on multiple scenarios in ‘Include’ or ‘Exclude’ mode.
- Ability to create queries based on the platforms e.g., iOS/iPadOS, Android, Windows 10 (in subsequent releases).
4. Compliance Policies
Compliance policies are a key feature of Intune. Intune compliance policies define the rules and settings for users and devices to maintain. Intune compliance policies can:
![]() Include actions that apply to devices that are noncompliant. Actions for noncompliance can alert users to the conditions of noncompliance and safeguard data on noncompliant devices.
Include actions that apply to devices that are noncompliant. Actions for noncompliance can alert users to the conditions of noncompliance and safeguard data on noncompliant devices.
![]() Be combined with Conditional Access, which can then block users and devices that don’t meet the rules
Be combined with Conditional Access, which can then block users and devices that don’t meet the rules
There are two parts to compliance policies in Intune:
Compliance policy settings: Tenant-wide settings that are like a built-in compliance policy which every device receives. Compliance policy settings set a baseline for how Compliance Policies work in your Intune environment. This includes whether devices that have not received any of these policies are compliant or noncompliant. These settings are not editable by individual organisations.
Device compliance policy: Platform-specific rules you configure and deploy to groups of users or devices. These rules define requirements for devices, like minimum operating systems or the use of disk encryption. Devices must meet these rules to be considered compliant.
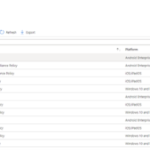 An example of what LAs can expect to see in the Compliance Policies section of Intune is shown.
An example of what LAs can expect to see in the Compliance Policies section of Intune is shown.
4.1 Configuration Profiles
Configuration profiles allow LAs to determine what settings are applied to a device that they would like to manage at their organisation. These profiles allow LAs to add and configure settings, and then push these settings to specific groups of devices, operating in a similar manner to group policies in SCCM.
Below are a few examples of what LAs can do using the configuration profiles:
![]() Allow or disable features
Allow or disable features
![]() Apply backgrounds
Apply backgrounds
![]() Set password rules
Set password rules
![]() Pin applications to the start bar
Pin applications to the start bar
![]() Allow or restrict specific policies
Allow or restrict specific policies
For a full list of configuration profiles which can be changed by LAs and instructions on how to create and assign configuration profiles for each device type please refer to the Operations Guide.
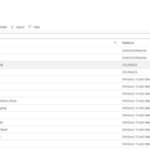 An example of what LAs can expect to see in the Configuration Profiles section of Intune is shown.
An example of what LAs can expect to see in the Configuration Profiles section of Intune is shown.
4.2 Conditional Access
Azure Conditional Access provides a means of securing access to Azure services, apps or data based on pre-qualified ‘conditions’ that are prescribed through policies. These Conditional Access Policies are configured by Central Tenant Administrators and applied to all users.
Please see our Conditional Access article for more information.
5. Enrolment Restrictions
Please note that there is a limit to the number of devices that can be linked to a user or administrator in NHSmail Intune. These limits apply to all device types: Windows 10/11, Surface Hubs, iOS/iPadOS, Android and HoloLens 2 devices.
| Role | Device Enrolment Restriction |
| Administrators | 15 Devices |
| Users | 5 Devices |
Please visit the Intune features document for more details.
| Last Reviewed Date | 14/03/2024 |
