1. Overview
This article provides an overview of the Intune Solution Architecture and Technical Model (including what this consists of). There is a brief description to summarise each item and what it does to help you better understand the model overall.
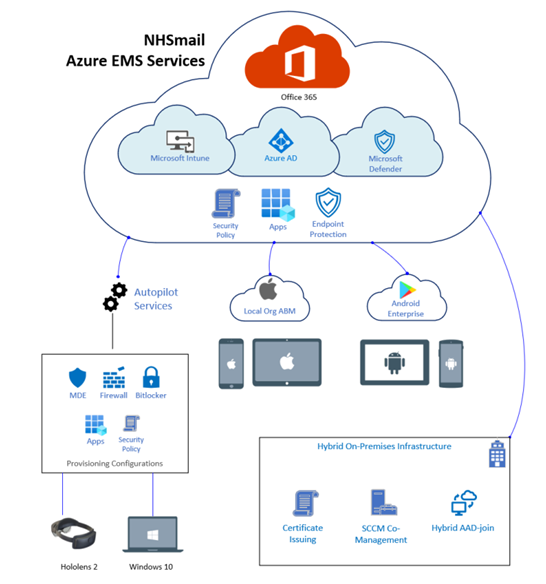
1.1 Intune Solution Architecture
The diagram below shows how all supported device types link into NHSmail Intune.
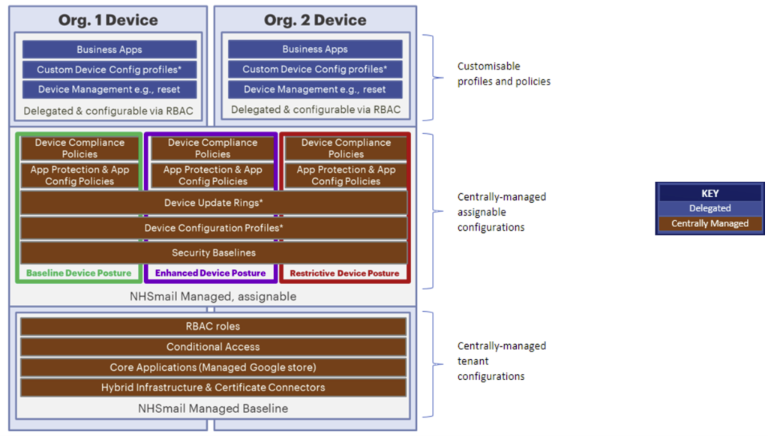
1.2 Technical Model
The diagram shows an overview of the Intune Technical Model, including which items LAs can customise and assign devices to:
2. Business Apps
Business Apps are apps that can be downloaded from your device app store:
| Android apps can be downloaded via the Intune Managed Google Play Store. | |
| iOS/iPadOS apps can be procured through ABM and deployed to Intune via the Volume Purchase Program (VPP) token. | |
 |
For Windows devices, the Microsoft 365 apps are built into Intune and can be configured and deployed to devices. You can also upload your own Windows apps (Win32) via the Intune Windows App section. |
These applications can be made mandatory or optional for users. For further information on how to deploy apps to devices please see the Operations Guide.
3. Device Compliance Policies and App Protection Policies
Device Compliance and App Protection will require alignment to 1 of 3 different postures.
3.1 Device Compliance
Device compliance policy settings are platform-specific rules which are configured and deployed to groups of users or devices. These rules define requirements for devices, like minimum operating systems or the use of disk encryption. Devices must meet these rules to be considered compliant.
Device Compliance policies are centrally managed; LAs will be able to view and assign these.
3.2 App Protection Policies (APP)
An additional layer of security is provided by application protection policies on Intune. App protection policies (APP) are rules that ensure an organisation’s data remains safe or contained in a managed app. Many productivity apps, such as the Microsoft Office apps, can be managed by Intune MAM.
- LAs can monitor the status of app protection policies applied to users from the App protection section in Intune.
- Personal devices cannot be enrolled in Intune. Therefore, to protect corporate data on personal devices we recommend to use App Protection Policies.
App Protection policies are centrally managed; LAs will be able to view and assign these.
3.3 Postures Available
There are 12 centralised policies available for Device Compliance and 6 centralised policies available for App Protection. These policies each have 3 different postures which come with varying degrees of complexity; alignment to one of these 3 postures is required.
- Baseline Posture: provides default security and compliance settings for simple use cases / test devices.
- Enhanced Posture: a more restrictive, but still mainstream posture. Aligns closely to the current ‘penciled-in’ configurations.
- Restrictive Posture: provides the most secure Intune configuration for high security/sensitivity use cases.
Examples of what the 3 different postures offer can be found in the table below:
| Item | Baseline | Enhanced | Restrictive | ||||||
| iOS/iPad OS | Android | Windows | iOS/iPad OS | Android | Windows | iOS/iPad OS | Android | Windows | |
| Minimum OS Version | iOS 15 | 8 | 10 (20H2) | iOS 16 | 10 | 10 (21H1) | iOS 16 | 11 | 10 (21H2) |
| Minimum Password Length & Type | 4
(Numeric) |
None | 6
(Numeric) |
6
(Numeric, Complex) |
Not Set | 6
(Alpha-numeric) |
6
(Alpha-numeric) |
Not Set | |
| Password Expiry | No Expiry | No Expiry | Not Set | 90 days | 90 days | Not Set | 60 days | 60 days | Not Set |
| Mark Device Non-Compliant | After 15 Days | After 15 Days | After 15 Days | Immediate | Immediate | Immediate | Immediate | Immediate | Immediate |
| Send Push Notification To User | 15 Days | 15 Days | Not Applicable | 3 Days | 3 Days | Not Applicable | Instant | Instant | Not Applicable |
4. Conditional Access (including Device Compliance)
Please see our Conditional Access (including Conditional Access & Device Compliance) Support Site article for more information.
5. Standard Device Configuration Profiles
Configuration profiles are policies or settings that configure devices (they operate in a similar manner to group policies in SCCM).
These profiles allow LAs to add and configure settings, and then push these settings to specific groups of devices.
Standard device configuration profiles are centrally managed; LAs will be able to view and assign these.
6. Custom Device Configuration Profiles
Custom configuration policies can be created and managed by LAs
LAs can use custom configuration profiles to manage what end users can do and see on their devices for example:
- Allow or disable features
- Set password rules
- Allow or restrict specific policies
- Apply backgrounds
- Pin apps to the start bar for all devices
Custom Device Configuration Profiles are delegated to LAs who have full control over these.
8. Autopilot Profile
Windows Autopilot deployment profiles lets you customize the out-of-box experience for your devices. Some examples include:
- Select your privacy settings
- Language
- Automatically configure your keyboard
Autopilot Profiles are centrally managed; LAs are able to view and assign these.
9. Enrolment Status Page
This shows apps and profile installation status to users during device setup. The enrolment status page appears during initial device setup and during first user sign in.
Enrolment Status Page is centrally manage; LAs are able to view and assign.
10. Exceptions
For all onboarded organisations that require any new custom configuration which sits outside of the predefined settings of the new three postures (as detailed in the Introduction section), Local Administrators are able to raise a Service Request (via Helpdesk Self-Service) for a custom policy or configuration to deployed for your organisation.
| Last Reviewed Date | 29/02/2024 |