Please note this information is correct at the time of publishing
Local Administrator (LA) bulletin – 07 Sept 2022 – Security reminders & best practice
Security questions review
Following recommendations from Cyber Security Operations Centre (CSOC) and NHS Digital it has been agreed that any account which utilises security questions and answers that are easy to guess, overly simplistic, or repetitive in nature would have their security questions changed and then set to “Marked As Compromised” as a precautionary measure.
The accounts identified were “Marked As Compromised” due to the security question and the answer being identical.
Direct communications were sent to the impacted organisations Primary Local Administrator (PLA) along with the account details.
There is an additional piece of work to identify and remediate accounts that have perceived weak security questions and answers.
Communications will be provided initially to the impacted user directing them to take remediation steps, followed by a direct communication to PLAs advising that action still needs to be taken. User and PLA remediation must be completed before 30 Sept 2022. If after this date no action is taken, Accenture will take action to remediate these accounts in bulk.
Recommend Local Administrator (LA) action – password reset process review
NHSmail and Cyber Security Operations Centre (CSOC) recommend that LAs carry out regular reviews of Helpdesk/Support Desk/ICT processes to ensure that adequate validation of users is taking place when performing a password reset.
Any reset completed over the phone must include the validation of security questions.
Failure to verify users attempting to reset a password could result in an unintentional breach or be as a result of a compromised account.
The NHSmail password policy can be found here
Multi-Factor Authentication (MFA) bulk edit coming to NHSmail
Currently organisations can configure MFA on NHSmail in several different ways:
- User management portal
- User policy settings
- Encouraging users to self-enrol
In the upcoming Cotman portal release (scheduled for mid-September) this will be changing.
MFA will no longer be an option in the user policy settings, as generally there are mixed use cases for users within a policy that do not necessarily align with a phased roll-out approach for MFA e.g., a mix of clinical and desk-based staff.
A bulk edit feature will be introduced for Local Administrators (LAs) in the user management portal to enable MFA for specific cohorts of users, as required.
Users can continue to self-register, however we recommend that organisations have plans locally to ensure users are supported with alternative methods for MFA, such as FIDO tokens.
We would encourage organisations to begin assessing their staff profiles and use cases and to plan their roll-out MFA locally to enhance the security of the platform.
Further guidance and updates will be published on the NHSmail support site during September.
Self Service Password reset
The password self-service function will be unavailable for a period of at least 2 weeks from 31 August 2022.
For further details please visit: https://support.nhs.net/2022/08/information-selfservice-password-reset-function-unavailable/
Multi Factor Authentication (MFA) for key business accounts
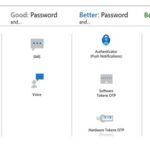
It is best practice for the Authenticator app to be used as the primary method of MFA wherever possible as per the image above.
For further information please visit the NHSmail support pages: https://support.nhs.net/knowledge-base/multi-factor-authentication-mfa/
Recommended Local Administrator (LA) – Spam/malicious email identification
Whilst measures are taken to prevent spam and phishing emails from being delivered to NHSmail users, we would ask that all users remain vigilant to spam and phishing emails and report any suspicious URL and emails to spamreports@nhs.net
Further information and guidance regarding spam or phishing emails can be found on the NHSmail support pages –Cyber Security – NHSmail Support
If you require additional help and support, the NHSmail helpdesk is available 24 hours-a-day, 7 days-a-week on 0333 200 1133 or by emailing helpdesk@nhs.net.
Compromised accounts guidance
We have recently updated the guidance around compromised accounts, one key piece of information is what is seen as a potential compromise.
A compromised account can typically be associated with behaviour that is deemed ‘not normal’.
This may be related to one or more of the following examples:
- A sudden increase in emails being sent
- The content within an email sent being inappropriate or malicious
- Account login activity occurring within unsociable timescales and showing a clear change from previous activity
To ensure the NHSmail platform and its users are protected from malicious activity where possible, Local Administrators (LAs) should mark an account as compromised in any case where they perceive an account to be behaving abnormally.
Additionally, an account can be marked as compromised as many times as an LA sees fit.
For further details on the process, please visit the NHSmail support pages – https://support.nhs.net/knowledge-base/compromised-accounts/
Best wishes,
NHSmail Team
NHSmail is provided by NHS Digital
in partnership with Accenture




