The NHSmail Bring Your Own Device solution provides security controls for an organisation’s Bring Your Own (BYO) devices that access NHSmail Office 365 (O365) services.
Please refer to the Overview article first, before reading the Local Administrator Guidance below.
The target audience for this guidance is Local Administrators. If you are a user with questions about the BYO device security controls, please contact your Local Administrator.
Introduction
BYO devices that are in scope for this solution are defined as mobile devices (Android, iOS and iPadOS) and desktop / laptop devices (Windows 10/11, MacOS and Linux) that access NHSmail O365 services and are:
- Personally owned by users and unmanaged
- Corporate owned by organisations but unmanaged, i.e. unknown to the NHSmail tenant, not enrolled to the NHSmail Intune service
The BYO device security controls come in the form of Conditional Access Policies (CAPs) which are mapped to security groups. Local Administrators will be able to opt-in or opt-out users in their organisation of different controls. Users become eligible for different security controls depending on their licences.
What are the licence requirements?
The BYO device security controls will be available using standard NHSmail licences. For the security controls to be applied, users will need to have the relevant licences assigned to them.
The minimum licence requirement is the Azure Active Directory Premium P2 (AADP2) licence.
Some additional security controls are available for users with:
- the AADP2 licence and the Enterprise Mobility + Security E3 (EMS E3) licence
- the AADP2 licence and the Enterprise Mobility + Security E5 (EMS E5) licence
- the AADP2 licence and Microsoft Defender for Cloud Apps
The type of licence a user is assigned will determine the Security Group they are allocated to, and therefore the CAPs that will be applied. Local Administrators will be responsible for the procurement and assignment of licences for users to be opted-in to the BYO device security controls.
How do the BYO device security controls work?
The BYO device security controls come in the form of Conditional Access Policies (CAPs). Conditional Access (CA) is a tool used by Azure Active Directory to bring signals together to make decisions. CAPs are “if / then” statements. For example, “if” a user is trying to access an O365 service from a personal laptop, “then” prompt the user for Multi-Factor Authentication.
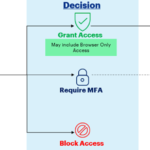
The BYO device solution CAPs will not apply to users in all circumstances as there are certain exceptions. To find out more about when the BYO device security controls will apply, please see below.
When will the security controls be applied to BYO device users?
The security controls will not apply if a user has not been added to the Security Groups. The security controls will only be applied to users once they are added to a Security Group. Once a user is removed from a Security Group all controls will cease to apply.
The security controls will not apply to users’ devices that are enrolled in Intune and are compliant. They will also not apply if the device is Hybrid Azure AD Joined (HAADJ).
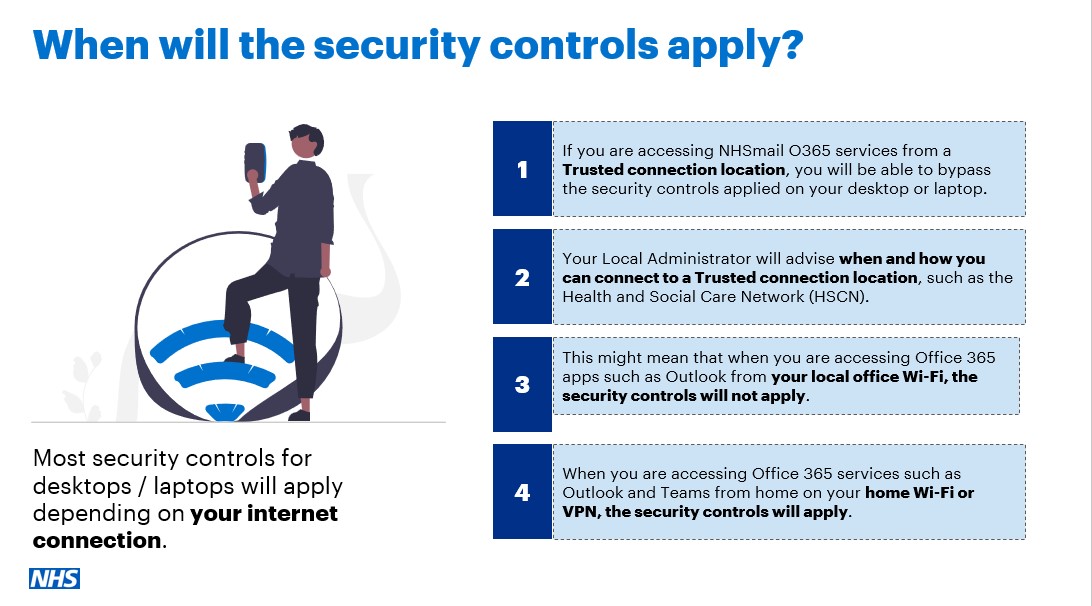
Most of the security controls will not apply if the user is accessing NHSmail O365 services from a BYO desktop or laptop device from a ‘Trusted Location’. They will apply when a user is accessing from an ‘Untrusted Location’. This refers to the user’s internet connection location.
A Trusted Location is a set range of IP addresses. When a user is connected to the internet via that IP range, the security controls will be applied to that user. This allows users to bypass restrictions when they are accessing the internet from a Trusted Location.
Currently, for the NHSmail BYO device security controls, the Health & Social Care Network (HSCN) is included in the BYO Trusted Location solution. This means that when a user is accessing NHSmail O365 services via the HSCN, the security controls will not apply.
If an organisation is not using the HSCN, Local Administrators can enquire about including additional IP addresses in the BYO Trusted Location solution range. This can be done by raising a query via the ServiceNow (SNOW) Raise a Request form. Please note that such requests will require a security review and will be assessed on a case-by-case basis.
When a user is accessing NHSmail O365 services from an Untrusted Location, such as their home Wi-Fi or through a VPN which routes internet traffic via the local connection, the relevant security controls will apply.
What security controls can be applied to BYO device users?
Local Administrators will be able to scope the users in their organisation and opt them into different security controls. Different security controls can be applied depending on the device type (e.g. desktop / laptop or mobile) and the licences users have been assigned. This section provides an overview of the available security controls, depending on the users’ licence type.
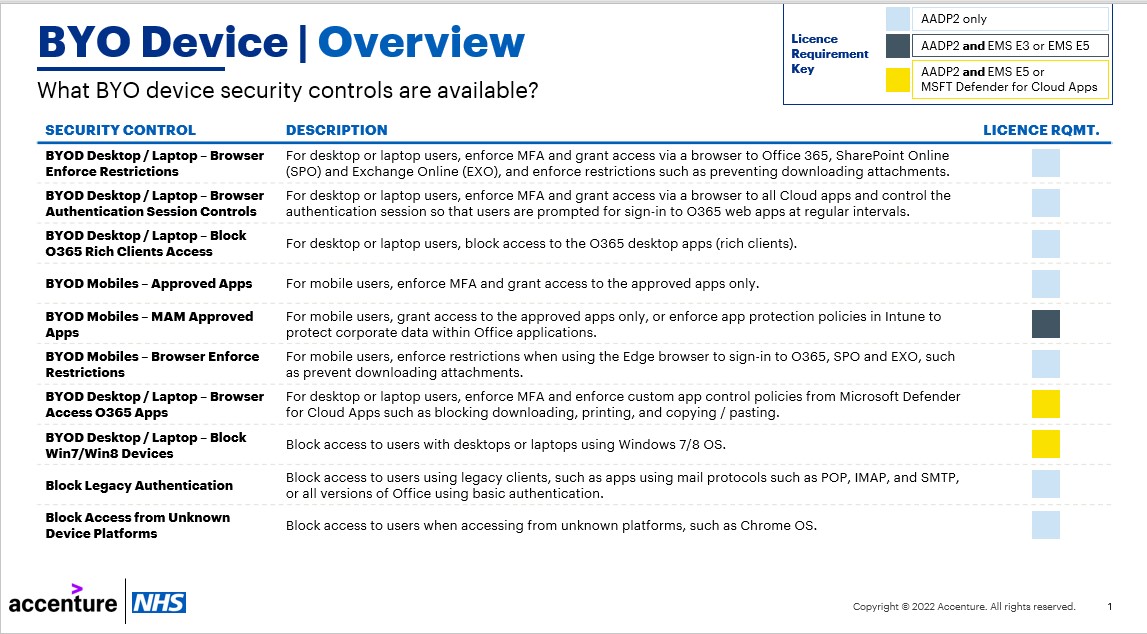
Summary of BYO device security controls
Please see below a summary of the BYO device security controls available.
| Security Control | Description | Licence Requirements |
| BYOD Desktop / Laptop – Browser Enforce Restrictions | For desktop or laptop users, enforce Multi-Factor Authentication (MFA) and grant access via a browser to Office 365, SharePoint Online (SPO) and Exchange Online (EXO), and enforce restrictions such as preventing downloading attachments. | AADP2 licence (per user). |
| BYOD Desktop / Laptop – Browser Authentication Session Controls | For desktop or laptop users, enforce MFA and grant access via a browser to all Cloud apps and control the authentication session so that users are prompted for sign-in to O365 web apps at regular intervals. | AADP2 licence (per user). |
| BYOD Desktop / Laptop – Block O365 Rich Clients Access | For desktop or laptop users, block access to the O365 desktop apps (rich clients). | AADP2 licence (per user). |
| BYOD Mobiles – Approved Apps | For mobile users, enforce MFA and grant access to the approved apps only. | AADP2 licence (per user). |
| BYOD Mobiles – MAM Approved Apps (EMS) | For mobile users, grant access to the approved apps only, or enforce app protection policies in Intune to protect corporate data within Office applications. Please note that for organisations onboarded onto Intune, users added into this policy must already have been added into an App Protection Policy posture. For more information, please refer to the NHSmail Intune Operations Guide here. | AADP2 and EMS E3 licence, or AADP2 and EMS E5 licence (per user). |
| BYOD Mobiles – Browser Enforce Restrictions | For mobile users, enforce restrictions when using the Edge browser to sign-in to O365, SPO and EXO, such as prevent downloading attachments. | AADP2 licence (per user). |
| BYOD Desktop / Laptop – Browser Access O365 Apps (EMS E5) | For desktop or laptop users, enforce MFA and enforce custom app control policies from Microsoft Defender for Cloud Apps such as blocking downloading, printing, and copying / pasting. | AADP2 and EMS E5 licence, or AADP2 and Microsoft Defender for Cloud Apps (per user). |
| BYOD Desktop / Laptop – Block Win7/8 Devices (EMS E5) | Block access to users with desktops or laptops using Windows 7/8 OS. | AADP2 and EMS E5 licence, or AADP2 and Microsoft Defender for Cloud Apps (per user). |
| Block Legacy Authentication | Block access to users using legacy clients, such as apps using mail protocols such as POP, IMAP, and SMTP, or all versions of Office using basic authentication. | AADP2 licence (per user). |
| Block Access from Unknown Device Platforms | Block access to users when accessing from unknown platforms, such as Chrome OS. | AADP2 licence (per user). |
Click onto the pack below for an overview of the BYO device security controls available.
Bring Your Own Device Security Controls Overview Pack
Detailed descriptions of the BYO device security controls
Please see below the detailed description of each BYO device security control. Please note that there may be minor differences in the error messages between the expected user behaviour stated below and the actual user behaviour depending on the BYO device Operating System (OS).
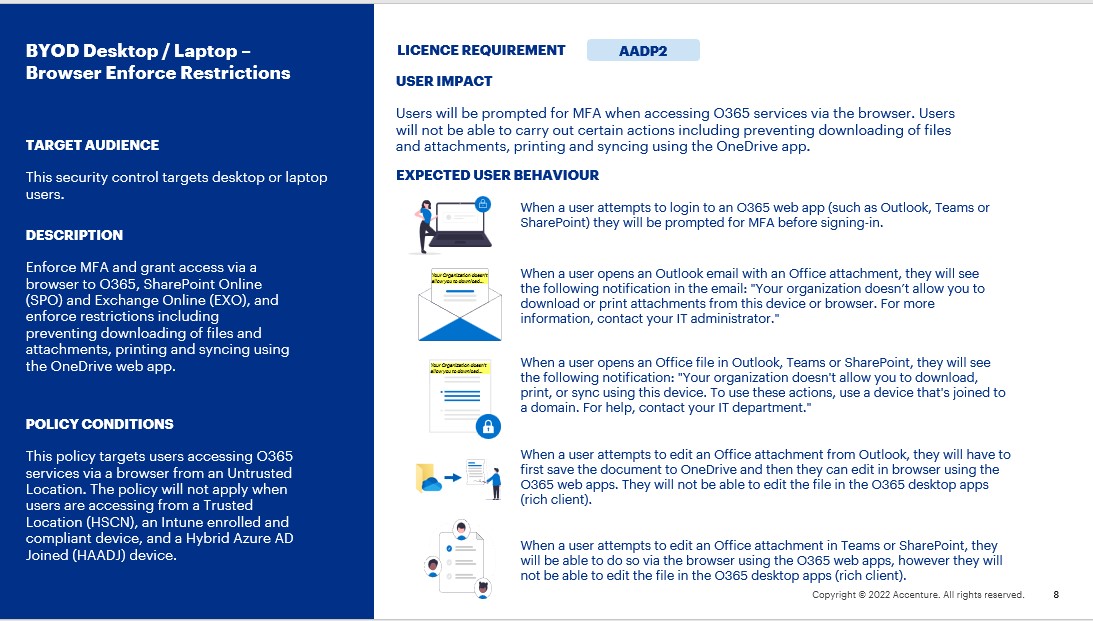
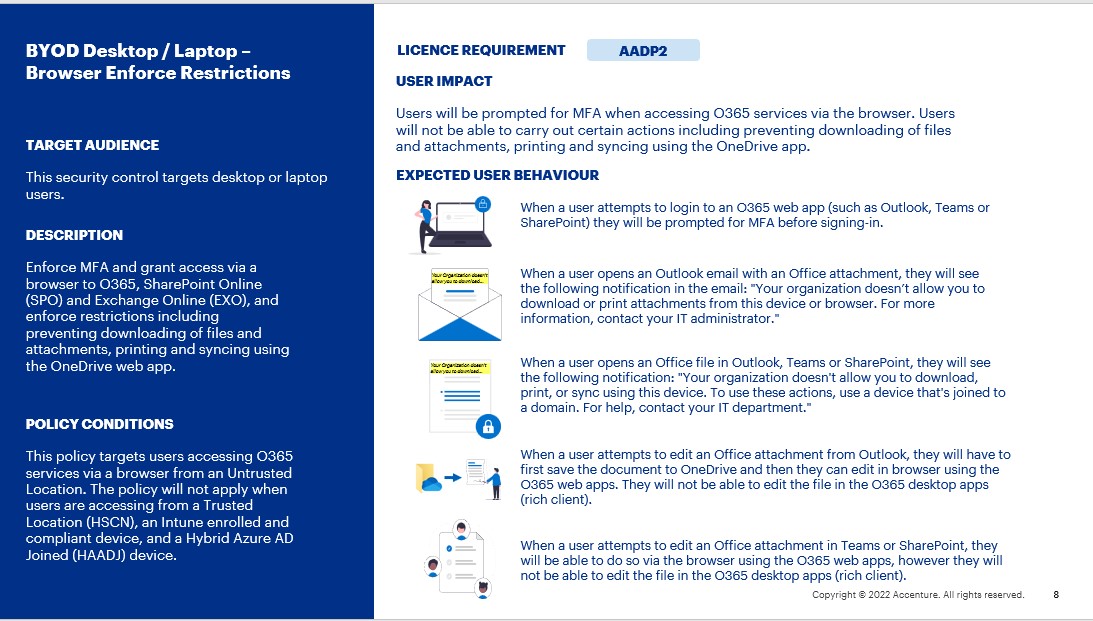
BYOD Desktop / Laptop – Browser Enforce Restrictions
Description:
This security control targets desktop or laptop users. It enforces MFA and grants access via a browser to O365, SharePoint Online (SPO) and Exchange Online (EXO), and enforces restrictions including preventing downloading of files and attachments, printing and syncing using the OneDrive web app.
Licence requirements:
This policy targets users with the AADP2 licence.
Policy conditions:
This policy targets users accessing O365 services via a browser from an Untrusted Location. The policy will not apply when users are accessing from a Trusted Location (HSCN), an Intune enrolled and compliant device, and a Hybrid Azure AD Joined (HAADJ) device.
User Impact:
Users will be prompted for MFA when accessing O365 services via the browser. Users will not be able to carry out certain actions including preventing downloading of files and attachments, printing and syncing using the OneDrive app.
Expected User Behaviour:
- When a user attempts to login to an O365 web app such as Outlook, Teams or SharePoint via the browser, they will be prompted for MFA before signing-in.
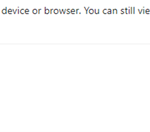
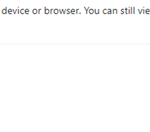
- When a user opens an Outlook email via the browser with an Office attachment, they will see the following notification in the email: “Your organisation doesn’t allow you to download or print attachments from this device or browser. For more information, contact your IT administrator.”
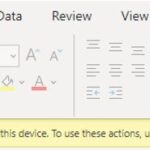
- When a user opens an Office file in the Outlook, Teams or SharePoint web apps via the browser, they will see the following notification: “Your organisation doesn’t allow you to download, print, or sync using this device. To use these actions, use a device that’s joined to a domain. For help, contact your IT department.” Therefore, the user will not be able to download or print the file, nor open the file in the O365 desktop apps (rich client).
- When a user attempts to edit an Office attachment from Outlook, they will have to first save the document to OneDrive and then they can edit in browser using the O365 web apps. They will not be able to edit the file in the O365 desktop apps (rich client).
- When a user attempts to edit an Office attachment in Teams or SharePoint, they will be able to do so via the browser using the O365 web apps, however they will not be able to edit the file in the O365 desktop apps (rich client).
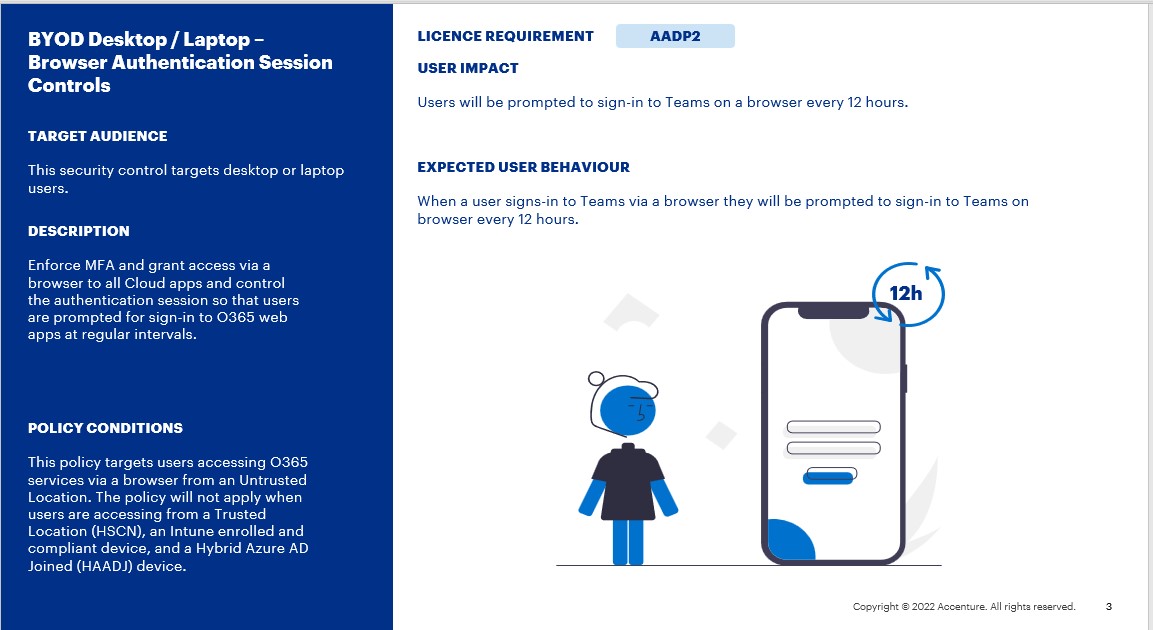
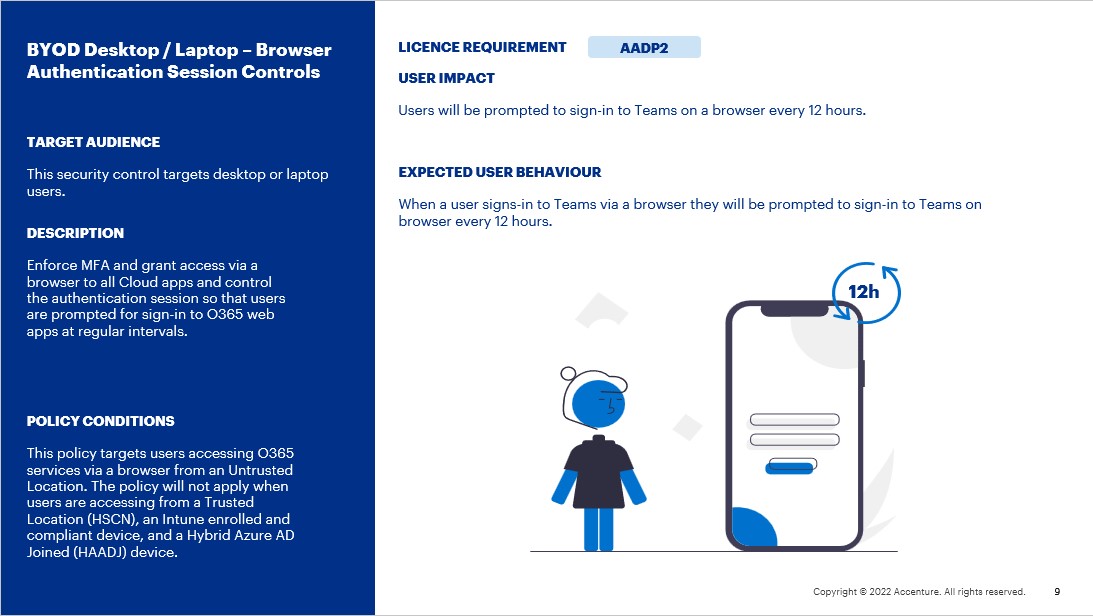
BYOD Desktop / Laptop – Browser Authentication Session Controls
Description:
This security control targets desktop or laptop users. It enforces MFA and grants access via a browser to all Cloud apps and controls the authentication session so that users are prompted for sign-in to O365 web apps at regular intervals.
Licence requirements:
This policy targets users with the AADP2 licence.
Policy conditions:
This policy targets users accessing O365 services via a browser from an Untrusted Location. The policy will not apply when users are accessing from a Trusted Location (HSCN), an Intune enrolled and compliant device, and a Hybrid Azure AD Joined (HAADJ) device.
User Impact:
Users will be prompted to sign-in to Teams on a browser every 12 hours.
Expected User Behaviour:
- When a user signs-in to Teams via a browser they will be prompted to sign-in to Teams on browser every 12 hours.
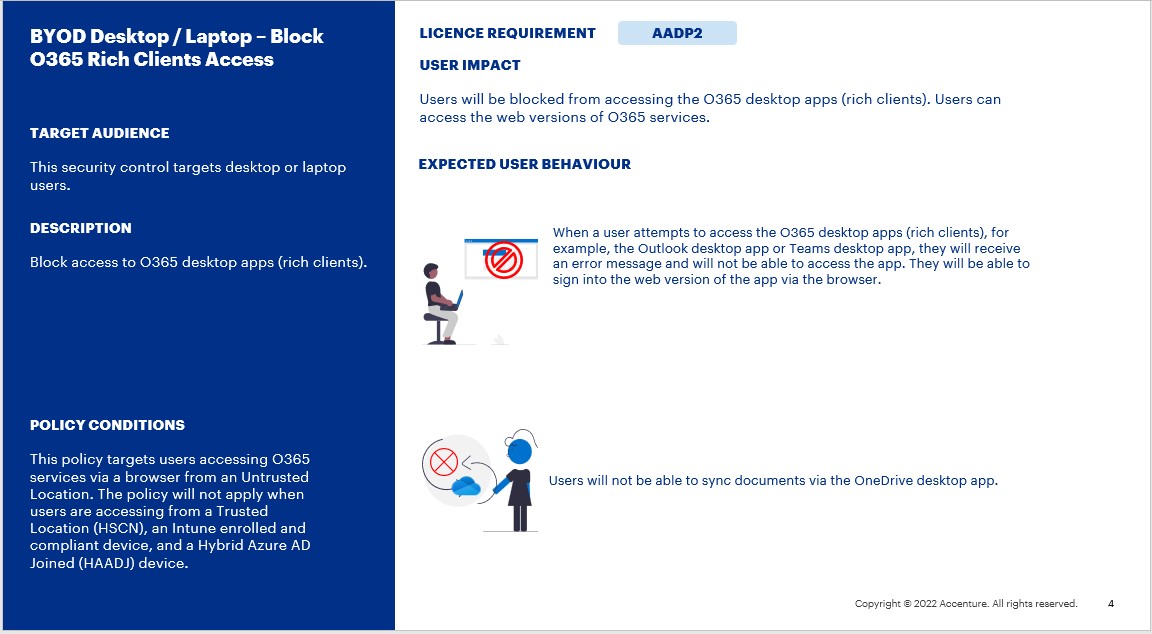
BYOD Desktop / Laptop – Block O365 Rich Clients Access
Description:
This security control targets desktop or laptop users. It blocks access to O365 desktop apps (rich clients).
Licence requirements:
This policy targets users with the AADP2 licence.
Policy conditions:
This policy targets users accessing O365 services via a browser from an Untrusted Location. The policy will not apply when users are accessing from a Trusted Location (HSCN), an Intune enrolled and compliant device, and a Hybrid Azure AD Joined (HAADJ) device.
User Impact:
Users will be blocked from accessing the O365 desktop apps (rich clients). Users can access the web versions of O365 services.
Expected User Behaviour:
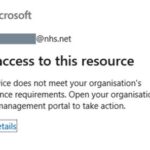
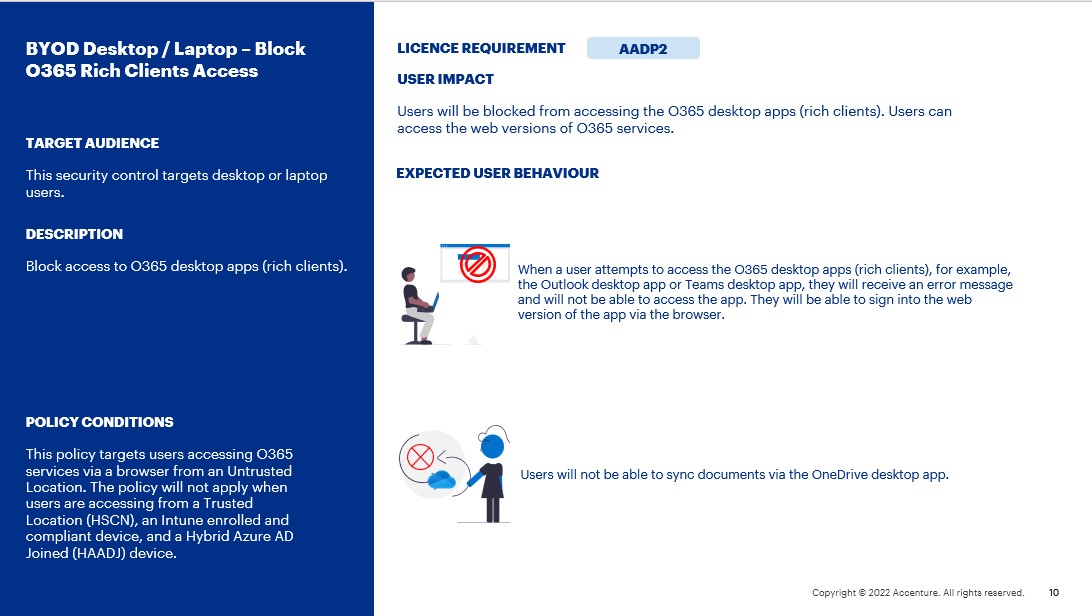
- When a user attempts to access the O365 desktop apps (rich clients), for example, the Outlook desktop app or Teams desktop app, if the device is not Azure AD registered, they will receive the below message and will not be able to access the app. They will be able to sign into the web version of the app via the browser.
-
- When a user attempts to access the O365 desktop apps (rich clients), for example, the Outlook desktop app or Teams desktop app, if the device is Azure AD registered, they will receive the below message and will not be able to access the app. They will be able to sign into the web version of the app via the browser.
- Users will not be able to sync documents via the OneDrive desktop app.
BYOD Mobiles – Approved Apps
Description:
This security control targets mobile users. It enforces MFA and grants access to the approved apps only.
Licence requirements:
This policy targets users with the AADP2 licence.
Policy conditions:
This policy targets users accessing O365 services on their mobiles.
User Impact:
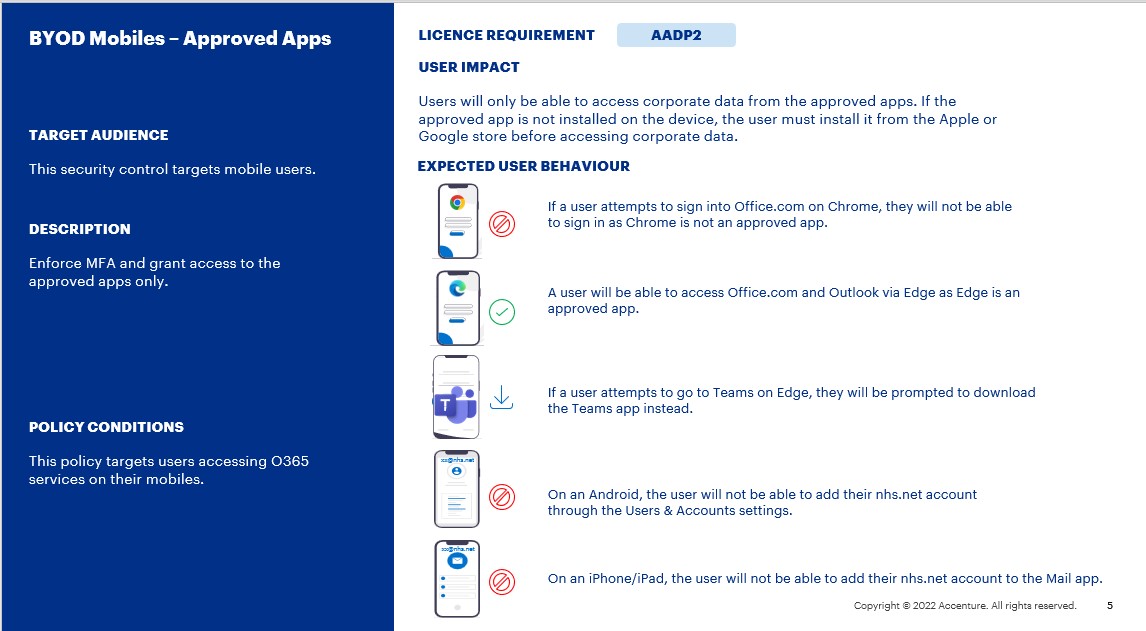
Users will only be able to access corporate data from the approved apps. If the approved app is not installed on the device, the user must install it from the Apple or Google store before accessing corporate data.
Expected User Behaviour:
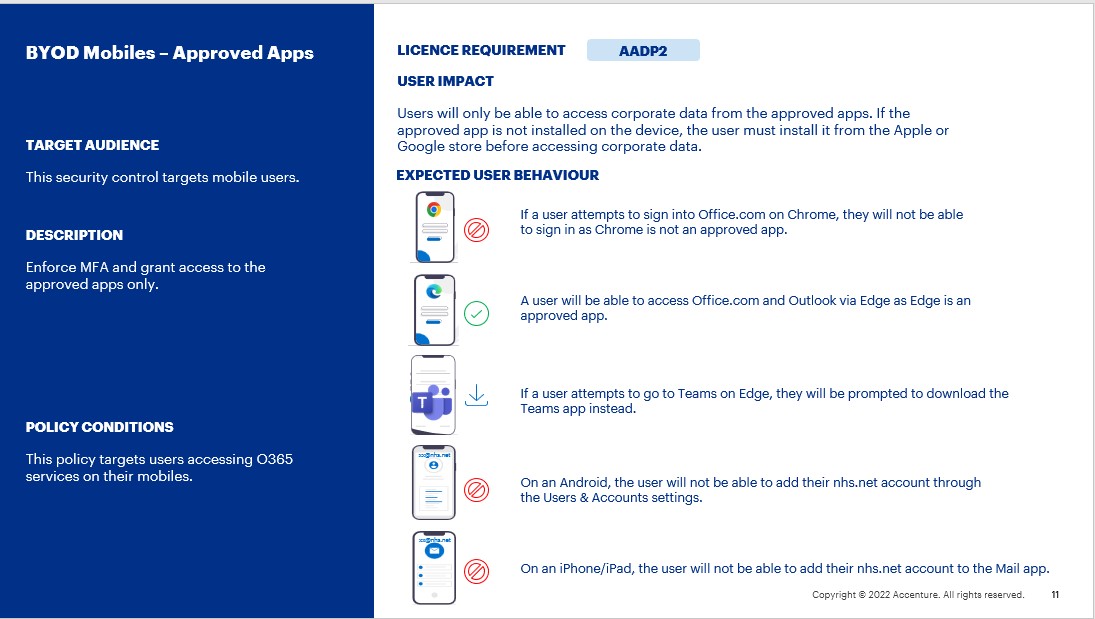
- If a user attempts to sign into Office.com on Chrome, they will not be able to sign in as Chrome is not an approved app.
- A user will be able to access Office.com and Outlook via Edge as Edge is an approved app.
- If a user attempts to go to Teams on Edge, they will be prompted to download the Teams app instead.
- On an Android, the user will not be able to add their nhs.net account through the Users & Accounts settings.
- On an iPhone/iPad, the user will not be able to add their nhs.net account to the Mail app.
BYOD Mobiles – MAM Approved Apps (EMS)
Description:
This security control targets mobile users. It grants access to the approved apps only, or enforces app protection policies in Intune to protect corporate data within Office applications. Please note that for organisations onboarded onto Intune, users added into this policy must already have been added into an App Protection Policy posture. For more information, please refer to the NHSmail Intune Operations Guide linked here.
Licence requirements:
This policy targets users with the AADP2 licence and the EMS E3 or EMS E5 licence.
Policy conditions:
This policy targets users accessing O365 services on their mobiles.
User Impact:
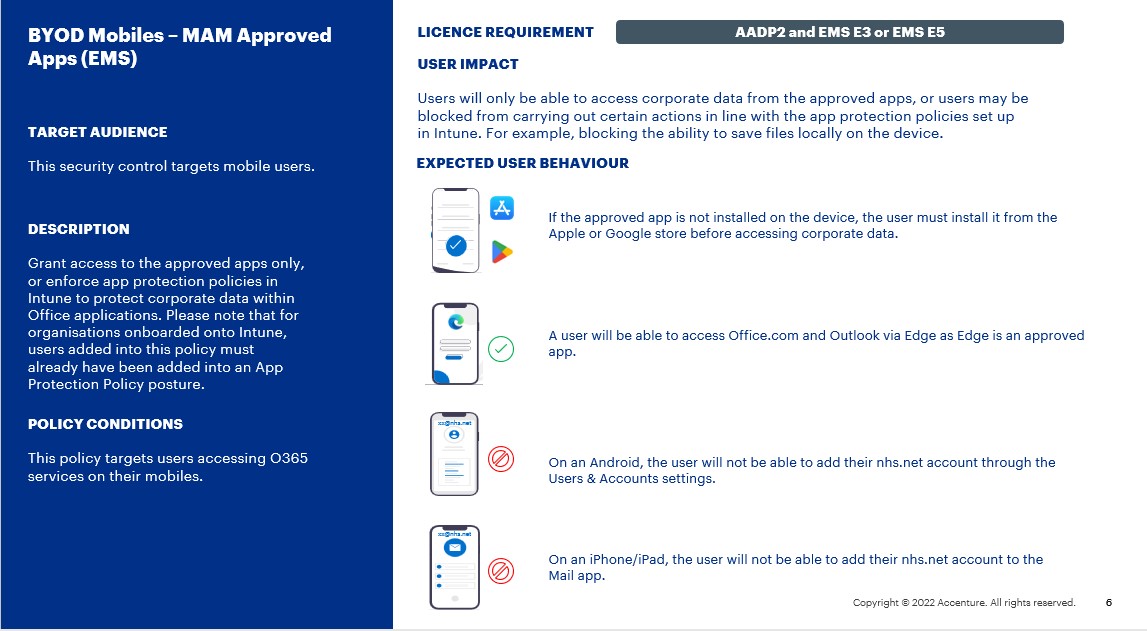
Users will only be able to access corporate data from the approved apps. If the approved app is not installed on the device, the user must install it from the Apple or Google store before accessing corporate data. Or users may be blocked from carrying out certain actions in line with the app protection policies set up in Intune, for example, blocking the ability to save files locally on the device.
Expected User Behaviour:
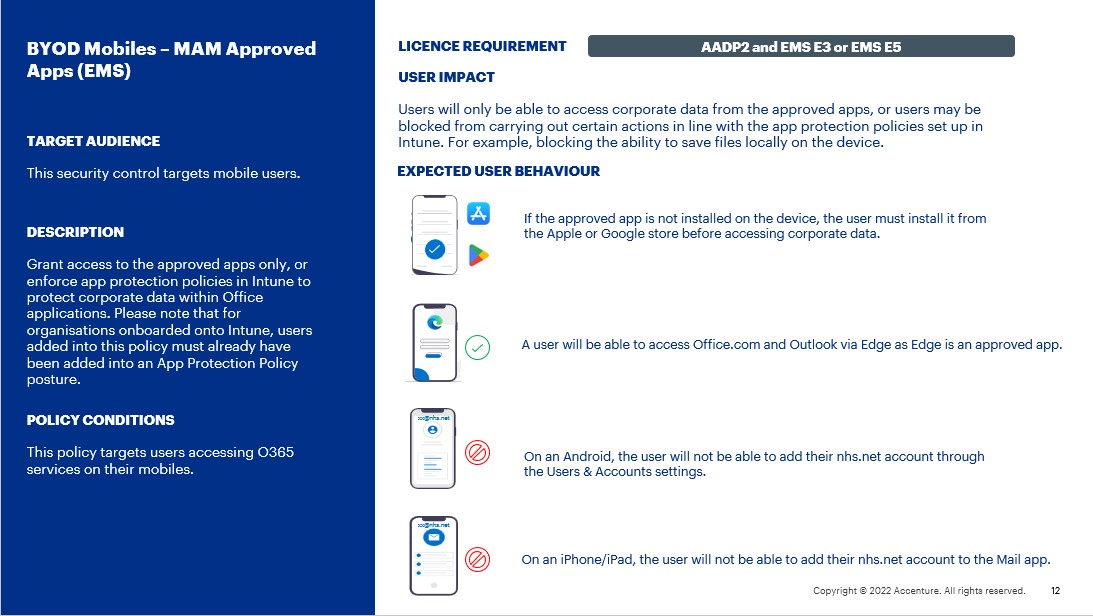
- A user will be able to set up Outlook on their device and see their emails.
- A user will be able to access Office.com via Edge.
- On an Android, the user will not be able to add their nhs.net account through the Users & Accounts settings.
- On an iPhone/iPad, the user will not be able to add their nhs.net account to the Mail app.
BYOD Mobiles – Browser Enforce Restrictions
Description:
This security control targets mobile users. It enforces restrictions when using a browser to sign into O365, SPO and EXO, such as downloading attachments.
Licence requirements:
This policy targets users with the AADP2 licence.
Policy conditions:
This policy targets users accessing O365 services on their mobiles.
User Impact:
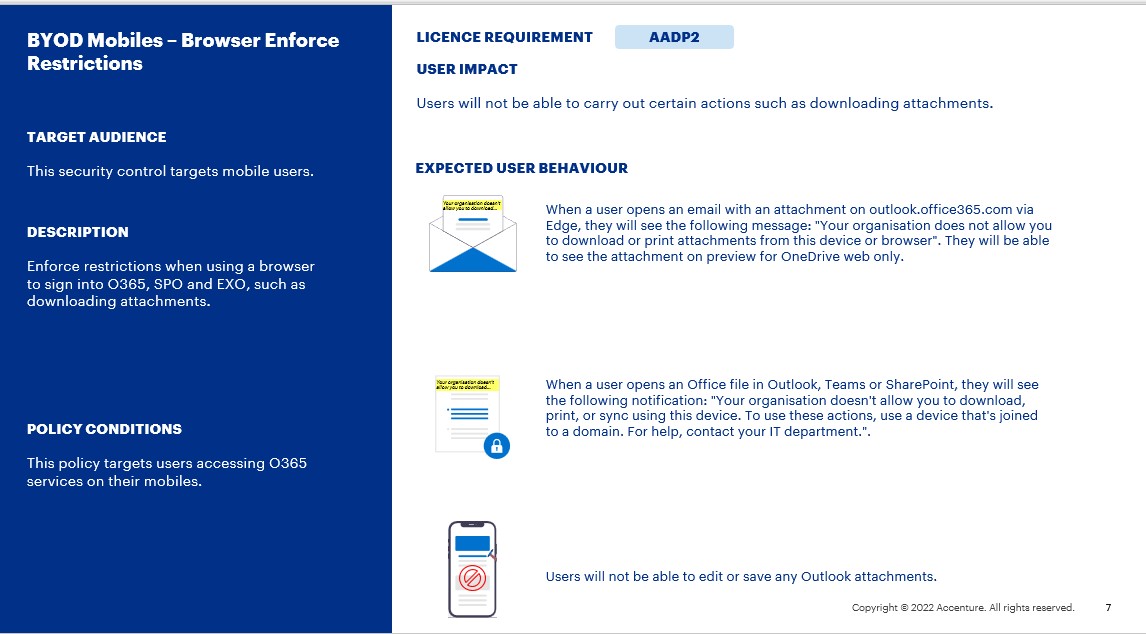
Users will not be able to carry out certain actions such as downloading attachments.
Expected User Behaviour:
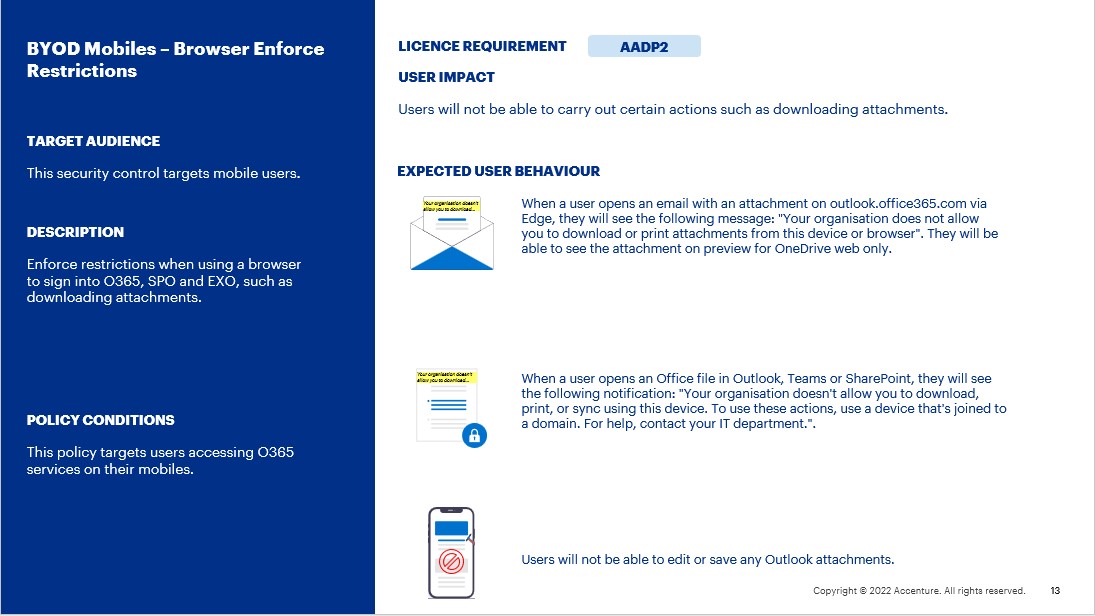
- When a user opens an email with an attachment on outlook.office365.com via Edge, they will see the following message: “Your organisation does not allow you to download or print attachments from this device or browser”. They will be able to see the attachment on preview for OneDrive web only.
- When a user opens an Office file in Outlook, Teams or SharePoint, they will see the following notification: “Your organisation doesn’t allow you to download, print, or sync using this device. To use these actions, use a device that’s joined to a domain. For help, contact your IT department.”.
- Users will not be able to edit or save any Outlook attachments.
BYOD Desktop / Laptop – Browser Access O365 Apps (EMS E5)
Description:
This security control targets desktop or laptop users. It enforces MFA and enforces custom app control policies from Microsoft Defender for Cloud Apps, such as blocking downloading, printing, and copying / pasting.
Licence requirements:
This policy targets users with the AADP2 licence and the EMS E5 licence or Microsoft Defender for Cloud Apps.
Policy conditions:
This policy targets users accessing O365 services via a browser from an Untrusted Location. The policy will not apply when users are accessing from a Trusted Location (HSCN), an Intune enrolled and compliant device, and a Hybrid Azure AD Joined (HAADJ) device.
User Impact:
Users will be blocked from carrying out certain actions in line with custom policies set up in Microsoft Defender for Cloud Apps.
Expected User Behaviour:
- When a user accesses an O365 service via the browser, they will have certain restrictions in line with custom policies on Microsoft Defender for Cloud Apps.
BYOD Desktop / Laptop – Block Win7/Win8 Devices (EMS E5)
Description:
This security control targets desktop or laptop users. It blocks access to users with desktops or laptops using Windows 7/8 OS.
Licence requirements:
This policy targets users with the AADP2 licence and the EMS E5 licence or Microsoft Defender for Cloud Apps.
Policy conditions:
This policy targets users accessing O365 services via a browser from an Untrusted Location. The policy will not apply when users are accessing from a Trusted Location (HSCN), an Intune enrolled and compliant device, and a Hybrid Azure AD Joined (HAADJ) device.
User Impact:
Users will be blocked from accessing Office 365 apps on a Windows 7/8 device.
Expected Behaviour:
- If a user attempts to access an O365 app from a Windows 7/8 device, they will be blocked from doing so.
Block Legacy Authentication
Description:
This security control blocks access to users using legacy clients, such as apps using mail protocols like POP, IMAP, and SMTP or all versions of Office using basic authentication.
Licence requirements:
This policy targets users with the AADP2 licence.
Policy conditions:
This policy targets users accessing O365 services from legacy clients.
User Impact:
Users will be blocked from using legacy clients.
Expected Behaviour:
- If a user attempts to access an Office 365 app using a legacy client, they will be blocked from doing so.
Block Access from Unknown Device Platforms
Description:
This security control blocks access to users when accessing from unknown platforms, such as Chrome OS.
Licence requirements:
This policy targets users with the AADP2 licence.
Policy conditions:
This policy targets users accessing O365 services from unknown platforms.
User Impact:
If a user attempts to access an Office 365 services using an unknown platform, such as Chrome OS, they will be blocked from doing so.
Expected Behaviour:
- A user will not be able to access O365 services using unknown platforms, such as Chrome OS.
What should organisations consider before adopting the BYO device solution?
Before organisations adopt any of the BYO device security controls, Local Administrators must consider the following.
- Local Administrators must review all relevant guidance to ensure a full understanding of the security controls that will be applied to users and the impact on their work.
- Local Administrators must carefully consider which users they will be opting-in to the BYO device security controls. The impact on users’ work and access to NHSmail services should be considered. For example, some clinical staff may require access to the O365 desktop apps (rich clients) for their work on clinical systems.
- The BYO device security controls can only be applied once the relevant licences have been assigned to the users. Local Administrators are advised to review and confirm the licences each user has through the user policy management section of the Portal. The minimum licence requirement is the Azure Active Directory Premium P2 (AADP2) licence.
- If users have not already registered for MFA, when the BYO device security controls are applied, users will be prompted to register for MFA before they can access O365 services. To minimise disruption, Local Administrators are advised to ensure all users set to be included in the security controls have already be registered for MFA. Please see here for further information on how users can enrol onto MFA and see here for further information about MFA.
- Local Administrators must ensure all relevant stakeholders have been communicated to ahead of the BYO device solution implementation, including seeking relevant approvals.
- Local Administrators must ensure users receive communications and advance warning ahead of this change.
A communications template has been prepared to help inform relevant stakeholders of the upcoming changes.
Click onto the pack below for resources that will help Local Administrators explain the BYO device security controls to users and can be tailored as per the controls applied for your users.
Bring Your Own Device Security Controls User Information Pack
How can organisations implement the BYO device solution?
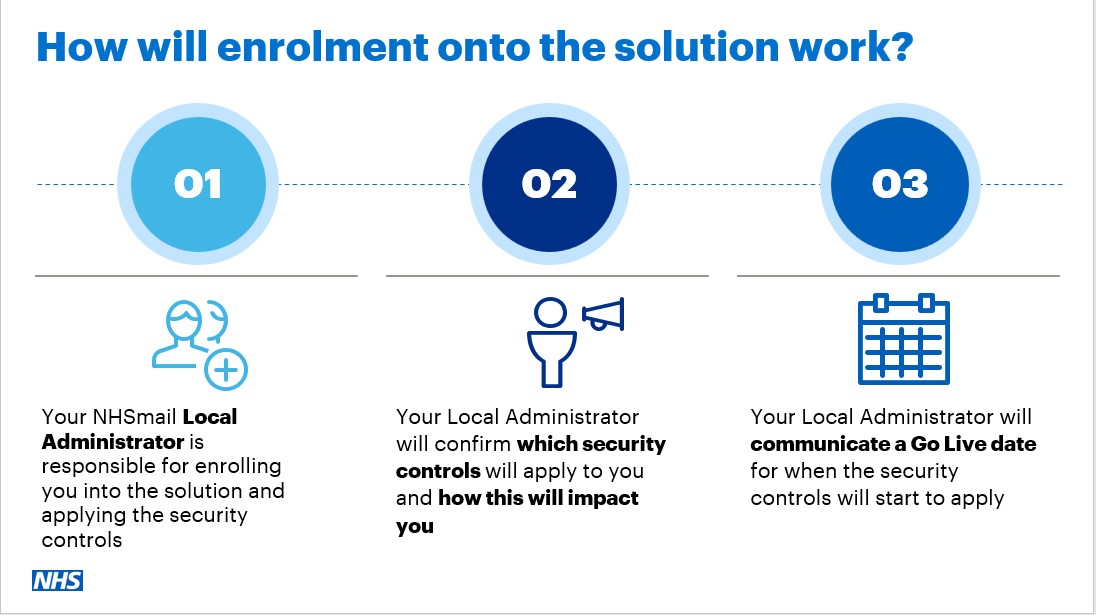
Once all pre-requisites have been considered, Local Administrators must follow the steps below to onboard users in their organisation.
- Create a static non-mail-enabled Security Group via the NHSmail Portal and add all users you would like to include in the security controls. Please note that this Security Group must not contain any nested Security Groups. For information about how to create and manage Security Groups via the NHSmail Portal, please review the Security Group Management guidance on the Support Site. The Security Group you have created will need to be added to the BYO device Global Security Groups by raising a Service Now (SNOW) form.
- Raise a request to onboard your organisation and enable your Security Group for the BYO device security controls via the ServiceNow (SNOW) Raise a Request form.
- You will need the following information to complete the form:
- Name and ODS code of the organisation for which the BYO device security controls will be implemented
- The name of the Security Group you have created
- The licences of the users to be opted-in to the security controls
- Once the form has been submitted, a member of the EMS Live Service Team will reach out to check all relevant pre-requisites have been met, confirm the security controls to be applied and finally, agree a Go Live date.
Once the Security Group you have created via the NHSmail Portal has been added to the BYO device Global Security Groups by the EMS Live Service Team, you can manage the membership of your Security Group via the NHSmail Portal. For information about how to update the membership and manage Security Groups via the NHSmail Portal, please review the Security Group Management guidance on the Support Site.
Local Administrators can address other issues by raising an incident via the ServiceNow (SNOW) Raise an Incident form.
What if organisations have a question about or an issue with the BYO device security controls?
Local Administrators can raise a query about the security controls via the ServiceNow (SNOW) Raise a Request form.
Local Administrators can raise an incident related to the security controls via the ServiceNow (SNOW) Raise an Incident form.
Frequently Asked Questions (FAQs)
Please ensure you have first reviewed all relevant guidance. If you have a question, you can raise a query about the security controls via the ServiceNow (SNOW) Raise a Request form.
Please ensure you have first reviewed all relevant guidance and understand the expected user behaviour. If you have an issue, you can raise an incident related to the security controls via the ServiceNow (SNOW) Raise an Incident form.
Network colleagues in your organisation should be able to confirm the routing of your O365 traffic and whether it goes via the HSCN.
If an organisation is unable to use the HSCN and is unable to enrol devices in Intune, Local Administrators can enquire about including additional IP addresses in the BYO device solution Trusted Location range. This can be done by raising a query via the ServiceNow (SNOW) Raise a Request form. Please note that such requests will require a security review and will be assessed on a case-by-case basis.
This is the expected user behaviour for the “BYOD Desktop / Laptop – Block O365 Rich Clients Access” security control. Users will be blocked from accessing the O365 desktop apps (rich clients) (for example the Outlook and Microsoft Teams desktop apps) on their desktop or laptop when accessing from an Untrusted Location, or from a device that is not enrolled to Intune or is non-compliant, or is not Hybrid Azure AD Joined (HAADJ).
Please direct users to access the browser versions of these applications.
Users can access the O365 rich clients when they are connected to the BYO Trusted Location (HSCN). Alternatively, you can enrol the user’s device into Intune or make it a Hybrid Azure AD Joined (HAADJ) device.
If you are experiencing further issues or you would like a user to be removed from the security controls, you can raise an incident related to the security controls via the ServiceNow (SNOW) Raise an Incident form.
You will need to create separate Security Groups depending on the licences users have been assigned, and therefore the security controls they are eligible for. Separate ServiceNow (SNOW) Raise a Request forms will need to be completed for each Security Group.
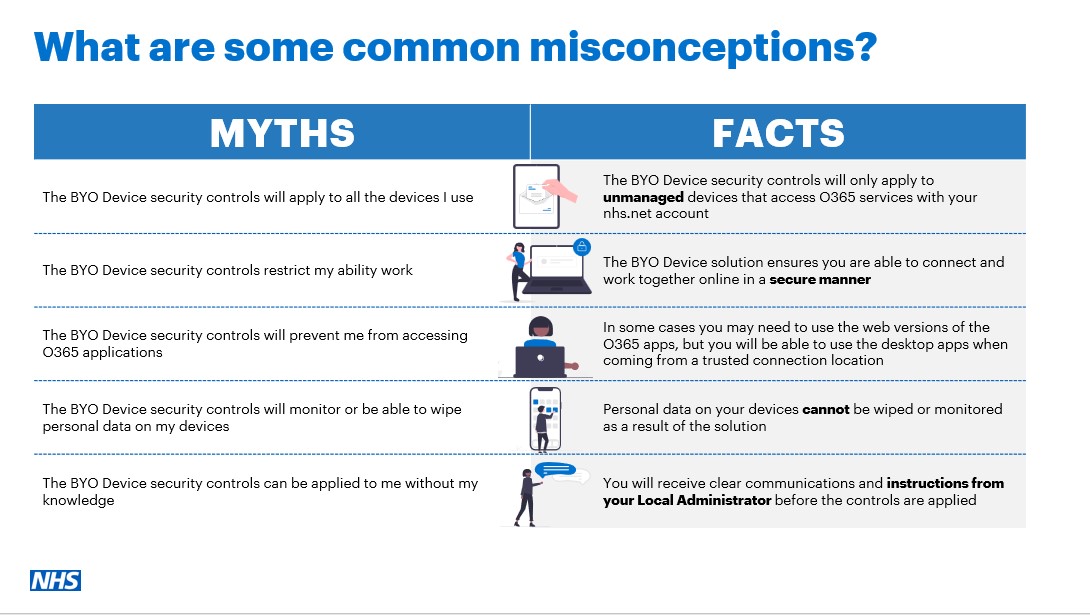
Personal data on BYO device cannot be wiped or monitored as a result of the BYO device security controls.
The BYO security controls apply to users, not to devices. Therefore, no device enrolment is required for this solution.
Once a user is added to a Security Group relevant access controls will be applied. Once a user is removed from the Security Group all controls will cease to apply.
| Last Reviewed Date | 08/09/2023 |