Organisations that use Transport Layer Security (TLS) to communicate with the Email Gateway
The Email Gateway supports opportunistic TLS, meaning, if an organisation’s MTA attempts to connect to the Email Gateway using TLS then it will use it. But, TLS is not enforced or required for a connection. This means that there is no end to end guarantee of encryption as your sending MTA may use TLS but when the relay service attempts to connect to the next hop to deliver the message after scanning that system may not support or use TLS.
The Email Gateway only supports message transfer on port 25 meaning all traffic (TLS or otherwise) should be directed to the Email Gateway over port 25 only.
The Email Gateway supports only a modern set of cipher suites. In order to successfully use TLS, a corresponding cipher suite must be used with the Email Gateway otherwise the connection will fail to be established. The following is a list of supported ciphers by the Email Gateway.
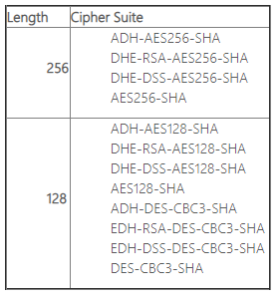
Note 1: It should also be noted that a number of these cipher suites do not meet UK Government or NHS security requirements.
Note 2: Although no longer supported for use, it has been found that Windows 2003 servers require a patch to match the cipher settings supported by the Email Gateway. The following Microsoft patch for Windows 2003 has successfully been deployed to alleviate default incompatibility (https://support.microsoft.com/en-us/kb/948963). This stated fix cannot be guaranteed in every circumstance.
| Last Reviewed Date | 9/4/2019 |
