What is Autopatch?
Windows Autopatch is a Microsoft-Managed service that automates the deployment and management of updates for select Microsoft Products, including:
- Windows Feature and quality updates
- Microsoft 365 Apps for Enterprise updates
- Microsoft Edge updates
- Microsoft Teams client updates
Devices are marked healthy / unhealthy to indicate update status and can be monitored in the Intune UI blades to examine the coverage of updates in your organisation’s estate.
Windows Autopatch creates an update framework similar to Windows Update rings and devices can be aligned to ‘fast’ and ‘slower’ update cadence in a similar way.
To read a detailed description of the capabilities and operation of this framework, refer to the Microsoft Windows Autopatch Documentation reference
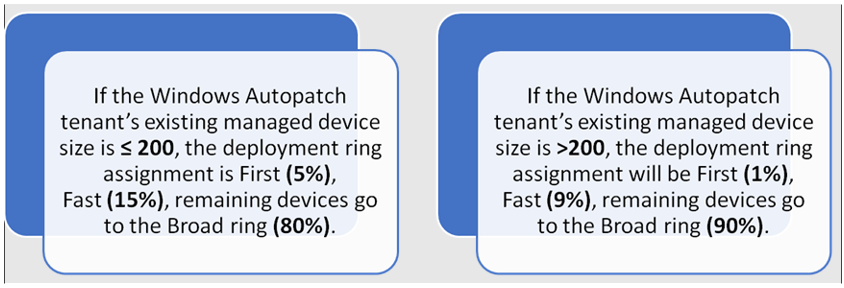
How Autopatch Works
Calculation Process
Pre-Requisites For Adopting Autopatch
Prior to adoption and deployment of this NHSmail implementation of
Autopatch, consider the following key points before committing to a full
production deployment.
1) Before committing devices into windows autopatch configuration,
consider windows device use settings (e.g. front line) when allocating
devices to the service. Carry out initial pilot testing before incorporating
a general population of devices.
2) Organisations choosing to use Windows Autopatch service should
ensure the following checks are completed beforehand:
| Check | Description |
| Windows OS build, architecture, and edition | Checks to see if devices support Windows 1809+ build (10.0.17763), 64-bit architecture and either Pro or Enterprise SKUs. |
| Windows update policies managed via Microsoft Intune | Checks to see if devices have Windows Updates policies managed via Microsoft Intune (MDM). If this the case, they should remove the devices the Windows update policy. |
| Windows update policies managed via Group Policy Object (GPO) | Checks to see if devices have Windows update policies managed via GPO and if so, remove the policy. Windows Autopatch doesn’t support Windows update policies managed via GPOs. Windows update should be managed via Microsoft Intune. |
| Microsoft Office update policy managed via Group Policy Object (GPO) | Checks to see if devices have Microsoft Office updates policies managed via GPO and if so, remove the policy. Windows Autopatch doesn’t support Microsoft Office update policies managed via GPOs. Office updates must be managed via Microsoft Intune or another Microsoft Office policy management method where Office update bits are downloaded directly from the Office Content Delivery Network (CDN). |
| Windows Autopatch network endpoints | There’s a set of network endpoints that Windows Autopatch services should be able to reach for the various aspects of the Windows Autopatch service. |
| Microsoft Teams network endpoints | There’s a set of network endpoints that devices with Microsoft Teams should be able to reach for software updates management. |
| Microsoft Edge network endpoints | There’s a set of network endpoints that devices with Microsoft Edge should be able to reach for software updates management. |
| Internet connectivity | Checks to see if a device has internet connectivity to communicate with Microsoft cloud services. Windows Autopatch uses the PingReply class. Windows Autopatch tries to ping at least three different Microsoft’s public URLs two times each, to confirm that ping results aren’t coming from the device’s cache. |
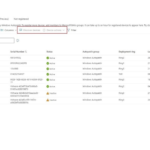
 3) The devices will be assigned to a Deployment Ring group, based on the
3) The devices will be assigned to a Deployment Ring group, based on the
calculation process described above. Device is listed as Registered in
the Windows Autopatch devices list:
How To Adopt Autopilot For NHSmail
Windows Autopatch is offered as an opt-in basis. Please raise a Service Request with the Intune Live Support team if you would like to use the functionality or if you have any questions.
Once you have raised a Service Request, the Intune Live Support team will carry out the following steps to enable Autopatch:
1) Intune Live Support will add an organisation’s Intune Admins who wants to use the service to the Azure AD group Modern Workplace Roles – Service Reader. Please note, LAs are unable to discover devices or do
any device actions from the Autopatch section. Currently, this feature
does not support scoped tags hence they will see all the Windows
devices using the service.
2) Intune Live Support will add the group that contains the organisation
Windows devices to the Windows Autopatch registration group.
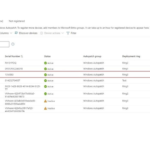
3) Intune Local Admins will see the updates assigned to a particular
Deployment ring from Autopatch blade however, they can get more
details on the current status by navigating to Window 10 updates and
select the profile linked to the deployment Ring.
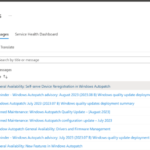 4) Under Windows Autopatch view from Tenant Admin, they can see the
4) Under Windows Autopatch view from Tenant Admin, they can see the
Messages board to monitor any changes on the service
| Last Reviewed Date | 09/08/2024 |