This article provides important information about the upcoming Security Baseline rollout.
What is the Security Baseline?
The Security Baseline is a set of Intune policies that will help to ensure devices connecting to NHSmail are equally protected at a fundamental level. The baseline will ensure that a minimum set of controls are in place when consuming M365 apps and services.
The scope consists of:
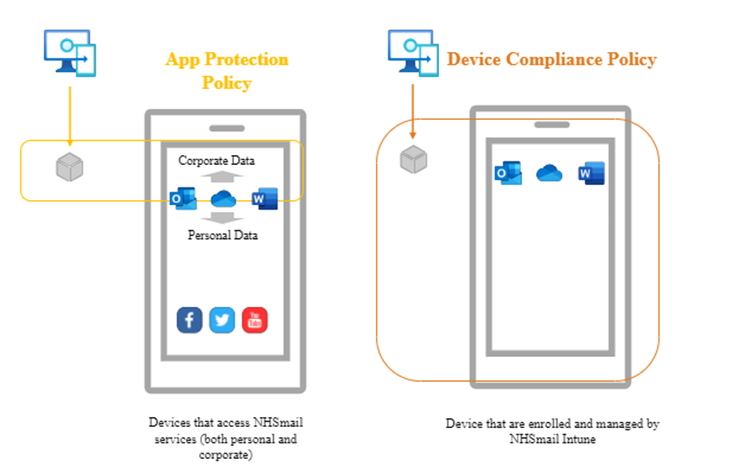
- App Protection Policies (APP) ensure a minimum criteria is being met on mobile devices belonging to users with a M365 Enhanced license , in order to access M365 apps (such as Outlook or Teams) using their @nhs.net account.
- Device Compliance Policies allow Local Administrators to easily see which Intune-managed devices are not meeting the minimum expected level of compliance (e.g. jailbroken device, OS out-of-date).
The plan is for the baseline to be automatically rolled out over a series of releases to all users of the NHSmail Enhanced Service, starting with organisations onboarded to NHSmail Intune.
Further details on schedule and next steps will be communicated in due course.
Why is it needed?
Organisations may have different security configurations to suit their individual needs. Whilst some controls will always be determined locally, introducing the new baseline will ensure that devices belonging to Intune users and accessing NHSmail services meet a minimum level of compliance that we should all be adhering to.
This will help us to further secure our environment as the baseline is aligned to the National Cyber Security Centre (NCSC) and Center for Internet Security (CIS) to satisfy what we are all expected to have in place, to keep NHS data and users secure.
It is important to note, the baseline is designed to support your organisation’s current environment, with changes not affecting any of your organisation’s policies that are more secure than those being introduced.
What are App Protection and Device Compliance Policies?
App Protection Policies
Intune App Protection Policies (APP) are used to keep your organisation’s data safe within core M365 apps on mobile devices.
They protect data at the application level, not the device level so, even if the user’s device isn’t enrolled in Intune, the App Protection Policies will still be able to manage how NHS data is shared and accessed. As part of the new baseline, App Protection Policies can be used to secure NHS data on both personal and corporate devices, by applying controls to core M365 apps.
Device Compliance Policies
Intune Device Compliance Policies determine what settings are expected to be met on Intune-managed devices, for them to be considered compliant. They improve the security status and compliance of managed devices by ensuring that devices adhere to specific standards.
If a managed device does not meet one or more of the compliance checks, then it will be marked as non-compliant in Intune. This will help Local Administrators when viewing devices and understanding potential reasons for non-compliance. As part of the new baseline, device Compliance Policies will only be applied to Intune-managed devices.
Who will be affected?
At this initial stage, the baseline will be rolled out to all Intune licensed users who are part of Intune onboarded organisations. The baseline will apply to both Intune managed and unmanaged devices.
What Controls are Being Introduced?
Release 1:
Release 1 is focused on creating a foundation for the baseline, so involves low impact security settings with minimum user impact. If your organisation already uses App Protection Policies, then you may have a number of these settings configured already.
The controls that will be rolled out in Release 1 can be seen in the table below.
Release 1 App Protection Policy Controls
| Control | iOS | Android | Description |
| Authenticator app installed | Required | N/A | The Authenticator app acts as a broker for the App Protection policies. Users will be prompted to install the app if not already installed. |
| Company Portal app installed | N/A | Required | The Company Portal app acts as a broker for the App Protection policies. Users will be prompted to install the app if not already installed. |
| Recheck the Access Requirements after (Minutes of inactivity) | 30 Minutes (Default Value)
|
30 Minutes (Default Value)
|
The App protection settings will be checked in the background after a set number of minutes of app inactivity. |
| Offline grace period (minutes) | 7200 Minutes
Block Access |
7200 Minutes
Block Access |
Period in minutes after which a user will be required to sign in again to the app. |
| Offline grace period (days) | 90 Days
Wipe Data |
90 Days
Wipe Data |
Period in days after which protected app data for apps will be removed. Once re-registered, data access will be restored. |
| Disabled account | Block Access | Block Access | Control whether Disabled accounts will be granted access to protected apps |
| Jailbroken / Rooted devices | Wipe Data | Wipe Data | Controls what happens to any protected app data if the user’s phone is rooted or jail-broken |
| Min OS version | 16.0
Block |
10.0
Block |
Determines the minimum OS versions that are required |
| Apps in scope | Core Microsoft Apps | Core Microsoft Apps | Controls which apps are in scope. |
| Custom Apps | Not Configured | Not Configured | Not configured – Custom third-party apps have not been specified (and not all apps support Intune App Protection) |
| Encrypt Org Data | Required | Required | Encrypt all protected app data on any device |
| Encrypt Org Data on enrolled devices | N/A | Required | If a phone is Intune-enrolled, require that data is encrypted on the device |
| Play integrity verdict | N/A | Basic integrity and devices integrity
Block Access |
On by default. This is a background check that apps are verified |
| Require threat scan on apps | N/A | Block Access | On by default, a background Google vulnerability check of Apps Security |
| Play integrity verdict evaluation type | N/A | Check strong integrity | The type of evaluation used to verify that apps are genuine |
Release 1 Device Compliance Policy Controls
| Control | iOS | Android | Windows | HoloLens |
| Play Integrity Verdict | N/A | Check basic integrity & device integrity | N/A | N/A |
| Jailbroken Devices | Block | N/A | N/A | N/A |
| Minimum OS version | 16.0 | 10.0 | 10.0.19044 | 10.20348.1528 |
| Require encryption of data storage on device | N/A | Require | Require | Not Configured |
| Intune App runtime integrity | N/A | Require | N/A | N/A |
| BitLocker | N/A | N/A
|
Require | Not Configured |
| Secure Boot | N/A | N/A
|
Require | Not Configured |
| Code Integrity | N/A | N/A
|
Require | Not Configured |
| Firewall | N/A | N/A
|
Require | Not Configured |
| Trusted Platform Module (TPM) | N/A | N/A
|
Require | Not Configured |
| Antivirus | N/A | N/A | Require | Not Configured |
| Antispyware | N/A | N/A | Require | Not Configured |
As mentioned above, the baseline is being introduced to support your current environment. If you have existing policies that are more secure than those being introduced, these will not be affected.
Release 2
Release 2 controls will build on those introduced in Release 1, with controls focusing on system security settings such as:
- Minimum password length.
- Required password types.
- PIN and biometric settings.
The specific settings and policies that will be rolled out in Release 2 will be provided to you nearer to the time of release.
Release 3
Release 3 will introduce stricter controls to ensure that NHS.net is in line with National Cyber Security Centre (NCSC) compliance. The policies will introduce data controls to prevent the movement of sensitive data out of NHS.net such as:
- Introducing controls to prevent NHS data from being backed up to user’s personal / non-NHS clouds.
- Preventing users from sending organisational data to unprotected apps (copying text from an NHS document to a social media account).
- Disabling screen capture from protected apps.
The specific settings and policies for Release 3 will be provided to you nearer to the time of release and further consultation will take place with organisations before this later release proceeds.
What to expect next?
Ahead of each release, Local Administrators will receive an email that will detail any steps that they need to take. The email will also include:
- An invite to a webinar / a link to a webinar recording
- A link to Support Site Material
- An Administrator Guide
- An End User Guide
- An End User Comms Template
| Last Reviewed Date | 17/04/2024 |