This article provides an overview of the NHSmail Bring Your Own Device (BYOD) security controls solution and is intended as a guide for Local Administrators. If you are a user with questions about the BYO device security controls, please contact your Local Administrator.
The NHSmail BYOD solution provides security controls for BYO devices that access NHSmail Office 365 (O365) services.
What is ‘Bring Your Own Device’?
‘Bring Your Own Device’ (BYOD) is the practice of allowing employees to use personal / unmanaged devices for their work. For NHSmail, this means allowing users to access NHSmail O365 services from personal or unmanaged corporate devices.
What Counts as a ‘Bring Your Own’ Device?
The devices in scope for this solution are mobile devices (Android, iOS and iPadOS) and desktop / laptop devices (Windows, MacOS and Linux) that access NHSmail O365 services and are:
- Personally owned by users and unmanaged
- Corporate owned by organisations but unmanaged, i.e., unknown to the NHSmail tenant, not enrolled to the NHSmail Intune service
Devices not in scope include:
- Any managed devices
- Any devices that do not consume NHSmail O365 services
Why is This Important for NHSmail Organisations?
Whilst BYOD presents many benefits, it also presents key security and data protection risks. By adding security controls to BYO devices, this will help to mitigate these risks, whilst ensuring users are still able to work together online in a secure manner. Aligned with industry best practice, the controls will help keep user and patient data in a more protected environment and provide increased protection against cyber-attacks.
The security controls are available to all NHSmail organisations, regardless of whether the organisation has onboarded to the NHSmail Intune service.
How do the BYO Device Security Controls Work?
The BYO device security controls come in the form of Conditional Access Policies (CAPs). Conditional Access (CA) is a tool used by Entra ID to bring signals together to make decisions. CAPs are “if / then” statements. For example, “if” a user is trying to access an O365 service from a personal laptop, “then” prompt the user for Multi-Factor Authentication.
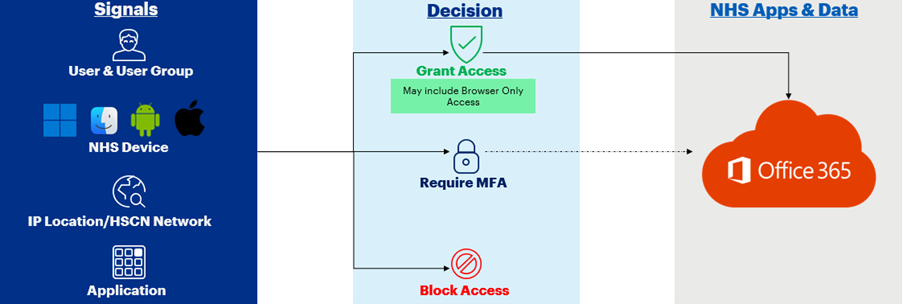
Organisations will be able to select from a range of Conditional Access Policies (CAPs) to apply security controls and restrict access to NHSmail O365 services based on, for example, device type, device location and operating system. Local Administrators will be able to opt-in or opt-out users in their organisation for different controls.
How Can Users Be Added To BYO Security Controls?
The security controls apply to users, not to devices. Therefore, no device enrolment is required for this solution. The primary component to allow organisations to scope users for the security controls are Entra ID Security Groups. The CAPs are mapped to these Security Groups. Once a user is added to a Security Group, relevant access controls will be applied. Once a user is removed from the Security Group, all controls will cease to apply.
However, the BYO device solution CAPs will not apply to users in all circumstances as there are certain exceptions.
- The security controls will not apply to users’ devices that are enrolled in Intune and are compliant.
- Most of the security controls will not apply if the user is accessing NHSmail O365 services from a BYO desktop or laptop device from a ‘Trusted Location’.
A Trusted Location is a set range of IP addresses. When a user is connected to the internet via that IP range, the security controls will not be applied to that user. When a user is accessing NHSmail O365 services from an ‘Untrusted Location’, such as their home Wi-Fi or through a VPN which routes internet traffic via the local connection, the relevant security controls will apply.
For the NHSmail BYO device security controls, the Health & Social Care Network (HSCN) is currently included in the BYO Trusted Location solution. This means that when a user is accessing NHSmail O365 services via the HSCN, the security controls will not apply.
If an organisation is not using the HSCN, Local Administrators can enquire about including additional IP addresses in the BYO Trusted Location solution range. This can be done by raising a query via the ServiceNow (SNOW) Raise a Request form. Please note that such requests will require a security review and will be assessed on a case-by-case basis.
What are the License Requirements?
For enhanced organisations with the national license, all licence requirements for conditional access are include by default.
What Security Controls can be Applied to BYO Device Users?
Local Administrators will be able to scope the users in their organisation and opt them into different security controls. Different security controls can be applied depending on the device type (e.g. desktop / laptop or mobile) and the licences users have been assigned. This section provides an overview of the available security controls, depending on the users’ license type.
BYO Device Security Controls
Please see below for a detailed description of each BYO device security control available.
BYOD Desktop / Laptop – Browser Enforce Restrictions
Description
Targets desktop / laptop users. It enforces MFA and grants access via a browser to Office 365 (O365), SharePoint Online (SPO) and Exchange Online (EXO). It also enforces restrictions including preventing the download of files and attachments, printing, or syncing using the OneDrive web app.
Policy Conditions
This policy targets users accessing O365 services via a browser from an Untrusted Location. The policy will not apply when users are accessing from a Trusted Location (HSCN), an Intune enrolled and compliant device, and a Hybrid Entra Joined (HAADJ) device.
User Impact
Users will be prompted for MFA when accessing O365 services via the browser. Users will not be able to carry out certain actions including downloading files and attachments, printing and syncing using the OneDrive app.
Expected User Behaviour
-
-
-
-
-
- When a user attempts to login to an O365 web app such as Outlook, Teams or SharePoint via the browser, they will be prompted for MFA before signing-in.
-
-
-
-
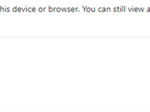
- When a user opens an Outlook email via the browser with an Office attachment, they will see the following notification in the email: “Your organisation doesn’t allow you to download or print attachments from this device or browser. For more information, contact your IT administrator.”
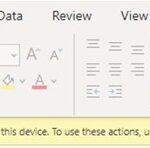
- When a user opens an Office file in the Outlook, Teams or SharePoint web apps via the browser, they will see the following notification: “Your organisation doesn’t allow you to download, print, or sync using this device. To use these actions, use a device that’s joined to a domain. For help, contact your IT department.” Therefore, the user will not be able to download or print the file, nor open the file in the O365 desktop apps (rich client).
-
-
-
-
-
- When a user attempts to edit an Office attachment from Outlook, they will have to first save the document to OneDrive and then they can edit in browser using the O365 web apps. They will not be able to edit the file in the O365 desktop apps (rich client).
- When a user attempts to edit an Office attachment in Teams or SharePoint, they will be able to do so via the browser using the O365 web apps, however they will not be able to edit the file in the O365 desktop apps (rich client).
-
-
-
-
BYOD Desktop / Laptop – Browser Authentication Session Controls
Description
Targets desktop / laptop users. It enforces MFA and grants access via a browser to all Cloud apps and controls the authentication session so that users are prompted for sign-in to O365 web apps at regular intervals.
Policy Conditions
This policy targets users accessing O365 services via a browser from an Untrusted Location. The policy will not apply when users are accessing from a Trusted Location (HSCN), an Intune enrolled compliant device, and a Hybrid Entra Joined (HEIDJ) device.
User Impact
Users will be prompted to sign-in to Office 365 apps on a browser every 12 hours.
Expected User Behaviour
When a user signs-in to Office 365 apps via a browser, they will be prompted to sign-in to Teams on browser every 12 hours.
BYOD Mobiles – MAM Approved Apps (EMS)
Description
Targets mobile users. Grants access to approved apps only or enforces app protection policies in Intune to protect corporate data within Office applications. For more information, please refer to the NHSmail Intune Operations Guide.
Policy Conditions
This policy targets users accessing O365 services on their mobiles.
User Impact
Users will only be able to access corporate data from core Microsoft apps. As a result of this, access via any other application (e.g., a native mail client) is blocked. This is to ensure that app protection policies can apply and protect the data, for example, blocking the user from saving sensitive work documents locally on a device.
Expected User Behavior
- A user will be able to set up Outlook on their device and see their emails.
- On an Android, the user will not be able to add their nhs.net account through the Users & Accounts settings.
- On an iPhone/iPad, the user will not be able to add their nhs.net account to the Mail app.
What Should Organisations Consider Before Adopting the BYO Device Solution?
Before organisations adopt any of the BYO device security controls, Local Administrators (LAs) must consider the following.
- LAs must review all relevant guidance to ensure a full understanding of the security controls that will be applied to users and the impact on their work.
- LAs must carefully consider which users they will be opting-in to the BYO device security controls. The impact on users’ work and access to NHSmail services should be considered. For example, some clinical staff may require access to the O365 desktop apps (rich clients) for their work on clinical systems.
- LAs must ensure all relevant stakeholders have been communicated to ahead of the BYO device solution implementation, including seeking relevant approvals.
- LAs must ensure users receive communications and advance warning ahead of this change.
How can Organisations Implement the BYO Device Solution?
The following steps can be followed to implement the BYO device solution:
- Raise a request to onboard your organisation for the BYO device security controls via the ServiceNow (SNOW) Raise a Request form. Please include the policies you would like to have applied.
- Once the form has been submitted, a member of the EMS Live Service Team will reach out to help onboard your users to the BYO security controls.
- Once the Security Group you have created via the NHSmail Portal has been added to the BYO device Global Security Groups by the EMS Live Service Team, you can manage the membership of your Security Group via the NHSmail Portal.
For information about how to update the membership and manage Security Groups via the NHSmail Portal, please review the Security Group Management guidance on the Support Site.
What if Organisations have a Question About or an Issue with the BYO Device Security Controls?
Local Administrators can raise a query about the security controls via the ServiceNow (SNOW) Raise a Request form.
Local Administrators can raise an incident related to the security controls via the ServiceNow (SNOW) Raise an Incident form.
| Last Reviewed Date | 14/10/2024 |